Table of Contents
We’ve seen software-as-a-service (SaaS) purchasing increase dramatically over the last decade, but nobody anticipated the massive spike in sales during the first few months of the pandemic.
In fact, while many industries faced considerable setbacks, SaaS spending rose an astounding 26% year over year from February to April 2020, driven primarily by employees adopting new cloud-based tools to work remotely. Just think how quickly Zoom became a household name, and you get the picture.
While SaaS applications offer immense benefits to hybrid and fully remote work environments, without proper oversight, they increasingly open up organizations to security breaches and compliance threats – and shadow IT.
Here’s why.
Unlike on-premise enterprise software, any employee with a credit card can purchase SaaS. It results in a proliferation of Shadow IT, aka applications used by employees without the IT team’s knowledge. Because these tools remain unknown, they circumvent normal risk assessment processes and can set up your organization for serious trouble.
A 2021 study by software security firm Randori supports these claims, with 74% of security leaders reporting more attacks since the onset of the pandemic, while 42% mention security breaches caused by shadow IT.
Organizations with hybrid or remote workers face the greatest risk of shadow IT. And with SaaS predicted to become the majority of all software by 2030, IT and security teams need to establish a SaaS Management playbook to mitigate and address Shadow IT.
Hybrid Work Poses Significant Shadow IT Risks
There’s no doubt SaaS helps employees work smarter and more efficiently, yet off-the-grid SaaS makes it nearly impossible for IT to perform security and compliance procedures, such as intrusion detection, penetration testing, and threat log management. Additionally, because shadow applications remain undiscovered, IT can’t implement traditional user-based security processes.
Without proper vetting, organizations face considerable risk of costly data breaches. A study from Forbes Insights and IBM of 353 IT executives found that roughly 20% of organizations experienced a cyber attack due to shadow IT, while a separate study conducted by IBM found the average data breach in the U.S. in 2024 costs $4.88M.
Shadow IT also increases the chances of non-compliance risks for regulations including Europe’s General Data Protection Regulation (GDPR), or the U.S. Health Insurance Portability and Accountability Act (HIPAA). These regulations mandate strict guidelines for how businesses handle sensitive consumer data, and enforce strict penalties for non-compliance. In 2021, healthcare data breaches cost an average $9.42 million.
How Widespread Does Hybrid Work Make Shadow IT?
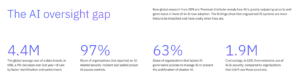
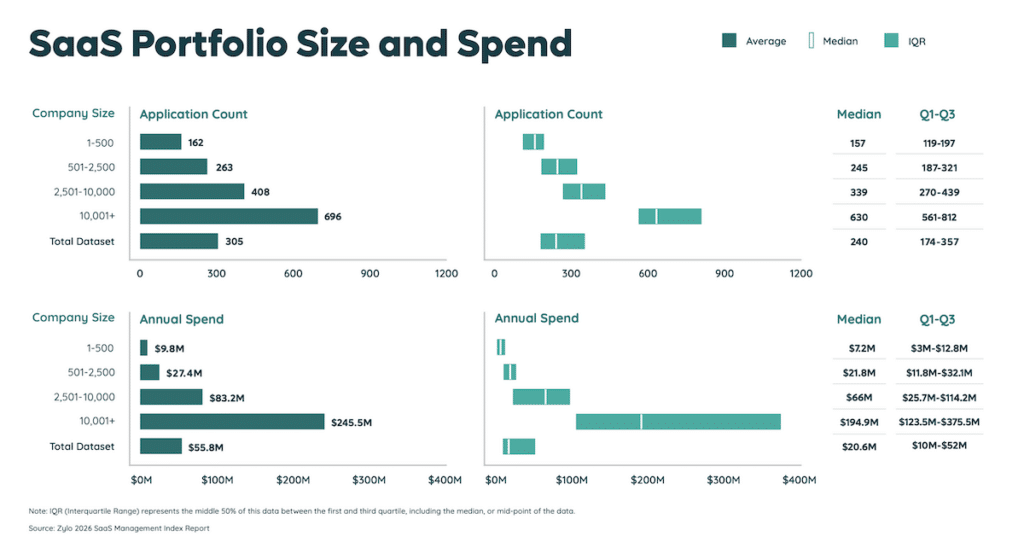
Shadow IT may not seem like a serious threat, mainly because most organizations significantly underestimate their inventory of existing SaaS. Today, organizations average 275 SaaS applications, yet underestimate the number by nearly 2X. Thanks, shadow IT.
Again, it all comes down to decentralized software purchases. Before the rise of SaaS, IT teams controlled a majority, if not all, of an organization’s software. Now, IT teams control roughly a quarter of all applications and 26% of SaaS spending, according to our research.
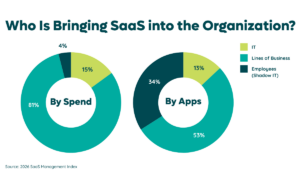
Even with the best of intentions, many organizations overlook shadow IT because they rely on manual processes, or self-reporting of SaaS purchases. It’s simply not practical to conduct SaaS discovery this way for a variety of reasons. Namely, because the typical company will see eight new applications enter its environment and three exit active use every 30 days.
Instead of reducing the number of SaaS tools across your organizations, consider establishing a SaaS Management process to discover and govern all shadow applications.
How the Zylo Discovery Engine Powers the Most Comprehensive SaaS Management Platform
Learn MoreUncover Shadow IT with a SaaS Management Strategy
Investing in a SaaS Management platform makes it easier to identify and eliminate shadow IT – especially in the world of hybrid work. Consider the following SaaS Management tips to help your organization boost innovation and ensure compliance in this new hybrid-work world:
-
Discover all SaaS applications
Manually keeping tabs on SaaS rarely works. Instead, consider a machine-learning equipped SaaS Management platform with application discovery capabilities. These solutions identify SaaS purchases in real-time by integrating with expense management systems, such as Expensify. They can even discover key information on application utilization (or lack thereof) and software renewal terms. - Communicate risks of shadow IT
There’s a strong possibility your fellow employees don’t fully understand the risk of utilizing unsanctioned software. And in a hybrid work environment with people spread around the country, communicating security risks and establishing processes for acquiring software becomes even more critical. - Set a strategy for SaaS Management
Remember, most organizations employ hundreds of applications, with many flying under the radar of IT. Establish a company-wide process for managing SaaS moving forward, assign roles and responsibilities, and make sure it becomes a top priority for your IT team. While you’re at it, define an approval process for all software purchases — even SaaS. - Determine IT-controlled tools
It’s okay to allow employees to manage SaaS tools, so long as IT gets looped into the process. On the other hand, enterprise-level tools should always fall under IT control. Decide which applications require IT oversight, and then determine the applications most suitable for departments or employees to manage.
Ready to learn how Zylo’s SaaS Management platform and shadow IT discovery tool can help your organization avoid risk and uncover your full application inventory? Reach out to schedule a personalized demo.

 Discover all SaaS applications
Discover all SaaS applications