
David Stoicescu: More SaaS, More Information Security Problems
Table of Contents ToggleEpisode SummaryGuest SpotlightEpisode HighlightsSaaS Management is a Team...
Back
Back
Search for Keywords...
Blog

Table of Contents
Maximizing your organization’s cybersecurity is probably something you think about a lot. After all, it’s critical to prevent data breaches and avoid hefty fees (potentially millions) for compliance violations. Not to mention, the integrity of your reputation may be at stake.
Often when we talk about cybersecurity, our heads quickly go to things like identity management, third-party data risk, and AI data security. Before getting tactical, it’s important to determine your organization’s security posture.
TechTarget defines security posture as “an organization’s overall cybersecurity strength and how well it can predict, prevent and respond to ever-changing cyberthreats.”
As the amount of SaaS in your organization grows, so too does your level of vendor and security risk. Practicing SaaS inventory management can help eliminate your blindspots and improve your organization’s security posture.
To dig into how, I sat down with Daven Combs, Director of Security at Zylo, and Dave Willis, VP of Technology Integrations at Netskope. Watch the conversation below or continue reading for insights on how SaaS management supports your security initiatives.
You already know how important maintaining your company’s cybersecurity is. The growth of SaaS will only make it more challenging and costly the longer it goes unaddressed.
Here’s why:
Daven Combs: It really comes back to how you can’t fix what you don’t know about. You can’t even fully communicate your organization’s risk and SaaS risk unless you know about the SaaS that your employees are using. Until you do, you won’t know about the company or customer data held within those programs.
I always confirm access to the application and any data within it is securely configured to meet your company’s policies or compliance needs.
It can also be extremely important to know that data is residing in approved geography. There can be serious data risks with embargoed countries and the like if you don’t know where your data is residing in these apps.
Also, visibility can actually help provide justification for projects that might otherwise be difficult to get funded.
Daven Combs: There’s far too much about shadow IT to handle in one webinar, but we can talk about how shadow IT is very unpredictable. There are a few key patterns you should keep track of:
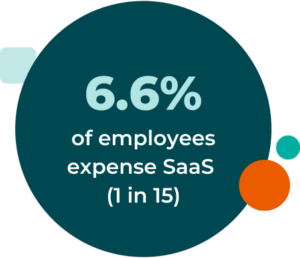 Unexpected problems that balloon to affect the entire industry. I think of the recent Webpack vulnerability for this one and how people thought it was a browser-side problem at first. However, it ballooned into an industry-affected data issue. It was almost impossible to address if you didn’t have the inventorying capabilities to handle it.
Unexpected problems that balloon to affect the entire industry. I think of the recent Webpack vulnerability for this one and how people thought it was a browser-side problem at first. However, it ballooned into an industry-affected data issue. It was almost impossible to address if you didn’t have the inventorying capabilities to handle it.Dave Willis: Netskope has also done a lot of work of chronicling all SaaS applications and identifying which ones pose the greatest risks—specifically through the lens of “trusted” personal apps causing data issues.
Shadow IT is only growing in danger because employees might have personal applications linked to work or used through work that cause data breaches and security risks. I can’t stress enough that visibility is the only real way to handle these problems.
Dave Willis: SaaS is inherently infrastructure that you cannot control, so you’re always opening yourself up to some risk there. As with all things, we’re in the business of mitigating risk, so you need to understand the relative risk a vendor poses. This is where vendor scoring comes in.
You want vendors who have scores indicative of security compliance and data integrity. These are the vendors who follow GDPR, Right to Be Forgotten, and all the other data rules you need to comply with. Netskope creates these scores so you can easily tell low-risk vendors from high-risk ones.
This helps you tell which vendors are safe to work with. But also it allows you to fine-tune your app usage and decide which types of apps are most important to have good risk scores. A minor app might not be as important for risk scoring, but a storage app definitely is.
Dave Willis: First, use a third-party trust assessment to see which applications should even be onboarded. Tools like Netskope and Zylo can help determine which apps are safest and on your “good” list.
Then, create a second layer of policy based on apps that are still safe but only certain groups need access to. Users are allowed to go to those sites with some form of justification page that says, “This is in the realm of acceptable because of the risk score, but you need to tell us why you’re going to it.” That can trigger other downstream, more official onboarding or risk assessment.
Last, create a blacklist of sites employees should not use, no matter what. These are sites that are dangerous and could threaten company data security.
In many cases, we have a permissive mindset – going back to when people started just having internet access at work. They don’t necessarily block these websites. But, they do prevent downloading and uploading anything to and from that site, because those are the two riskiest activities.
Daven Combs: Using Zylo would be a fantastic start. If you don’t have such a tool, ensure that you have a list, a way of creating that inventory, starting it or emboldening it, making it better. Start with what you know.
From there, look at what kind of authentication system you are using. See what people are going into. For example, look at Google and determine if you’re using Google authentication and have it enabled. If you don’t think you have it enabled, make sure you don’t.
Next, look at the apps in use that are free. They can be more important arguably than the ones that are paid for and under contract. Because, at that point, the user has no reason to go to you for access. They use it in whatever way they intend it to or someone else is going to.
After that, determine how those applications can be authenticated. If it’s not under central authentication using SAML, can it be? Many times people don’t understand that just because you have it configured with SSO SAML, it can still sometimes be authenticated with just username and password.
SaaS applications don’t all configure their authentication the same. Many people make assumptions with SAML that there’s no way anybody else can get in. That’s not true in a lot of cases.
If there’s a toggle for enforcing SAML, do that. If it makes sense and you look at it and say, this has to be done, do it with enough caution and education that you aren’t going to break anything. But, know that there’s a goalpost for what is right with getting connected into your applications.
That area is probably a good start for any group or company if they’ve already started adding this into it would be very important.
There are countless ways to improve your organization’s security posture – visibility into your SaaS stack and proper data management being integral.
That’s why Zylo has partnered with Netskope to power Security Detail. It provides instant visibility into SaaS attestations and certifications for the SaaS tools your teams rely on.
With powerful compliance and security data at your fingertips, you can:
Learn more about Security Detail, or schedule a demo to see how it works for yourself.
ABOUT THE AUTHOR

Ben Pippenger
Ben Pippenger is Staff Product Manager and Co-Founder of Zylo, where he helps enterprises maximize the value of their SaaS investments. With more than 20 years of experience in B2B software, Ben is a recognized thought leader in SaaS Management, license optimization, and IT strategy. Before founding Zylo, he held product and account leadership roles at Salesforce and ExactTarget. A self-proclaimed SaaS geek, Ben regularly speaks on topics like shadow IT, SaaS ROI, and software lifecycle management.

Table of Contents ToggleEpisode SummaryGuest SpotlightEpisode HighlightsSaaS Management is a Team...
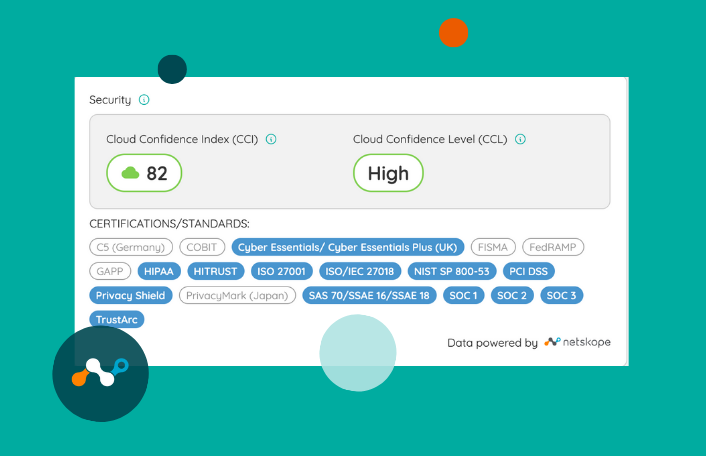
Table of Contents ToggleWhy Visibility Is Essential to Keeping Your Business...

Table of Contents ToggleEpisode SummaryGuest SpotlightEpisode HighlightsBusiness Savvy Is Non-Negotiable for...

Table of Contents ToggleDelivering Performance and SecurityEasily Assess Security Risks with...
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |