10/17/2023
Table of Contents
Modern companies have hundreds or even thousands of applications making up their SaaS stack. While these tools are great for productivity and collaboration, each one can also be a security risk for your organization.
Most organizations vet new SaaS applications prior to purchasing them. There are several aspects to consider when vetting new SaaS apps, such as information sharing capabilities, permission controls, and security. Also, ensuring that the apps are compliant with the applicable regulations pertaining to the business, its customers, and partners.
Unfortunately, security and compliance information is typically buried in SaaS vendors’ websites.
Imagine digging through hundreds of websites to find attestations and certifications for every application you have. What time would you have left to focus on strategic priorities and work? Likely, not much.
That’s why we partnered with Netksope, a recognized security leader, to bring the trusted security detail and risk scoring you need, natively into Zylo.
Why Visibility Is Essential to Keeping Your Business Secure
Information security and IT teams raise concerns about SaaS purchasing and usage, typically revolving around cybersecurity and privacy. Some risks, like data breaches and leaks, can result in severe penalties including fines, lawsuits, and a damaged reputation in your industry.
In the US, the average cost of a data breach is $4.88M, including mitigation efforts and lost business. This is why you need to know about every SaaS application in your business – not just IT managed applications – and the risk tied to each one.
Individual employees and business units can purchase new applications at any time, making security an even more daunting task.
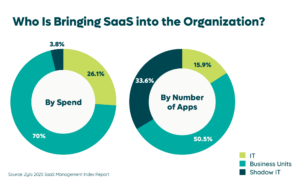
In fact, Zylo’s SaaS Management Index shows that shadow IT represents 33.6% of an organization’s apps. That means for the average organization with 275 applications, they have 92 applications that bypassed the usual vetting process – including a security review.
Further, shadow IT contributes to the dynamic nature of your SaaS environment, where the average organization sees six new SaaS applications every 30 days.
Ensuring your SaaS systems are compliant must be a continuous effort. Your IT and Information Security teams need insight into the compliance certifications of your SaaS applications to ensure your data and the data of your customers and partners is protected.
Identify Risk to Keep Your Business Safe with Zylo’s Security Detail, Powered by Netskope
Zylo and Netskope have partnered up to bring powerful security details, powered by Netskope, natively into the Zylo platform. By bringing Zylo’s unmatched SaaS discovery and inventory management together with Netskope’s robust database, companies are equipped to identify and manage risk.
Security Detail tracks the compliance status of your SaaS applications to help you identify risk and make confident renewal and purchase decisions. As new applications enter the business, you need to be able to identify risky purchases and whether or not your security standards are met. Security Detail makes this information instantly available for IT and Information Security teams to see where you need to invest time to reduce exposure to risk.
Today, the certifications and data center standards available in Zylo include:
- C5 (Germany)
- COBIT
- Cyber Essentials/Cyber Essentials Plus (UK)
- FedRAMP
- FISMA
- GAPP
- HIPAA
- HITRUST
- ISO 27001
- ISO/IEC 27018
- NIST SP 800-53
- PCI DSS
- Privacy Shield
- PrivacyMark (Japan)
- SAS 70/SSAE 16/SSAE 18
- SOC 1, SOC 2, and SOC 3
- TrustArc
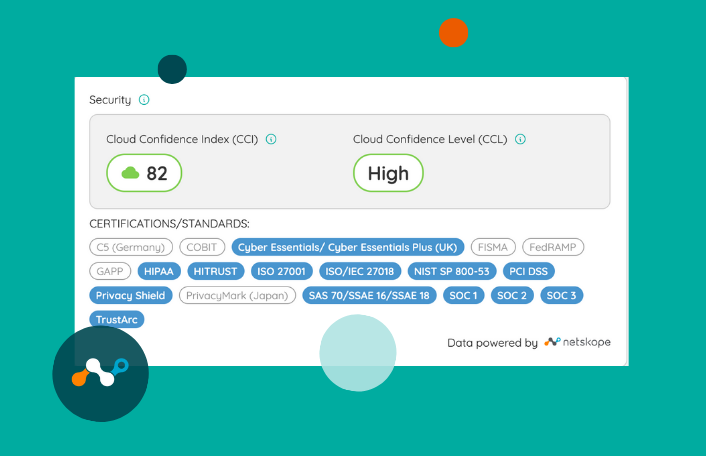
Additionally, this partnership brings the Netskope Cloud Confidence Index™ (CCI) to Zylo customers. CCI is a database of cloud apps that Netskope has evaluated based on objective criteria adapted from Cloud Security Alliance Guidance. These criteria measure the app’s enterprise readiness, taking into consideration an app’s security, audit-ability, and business continuity.
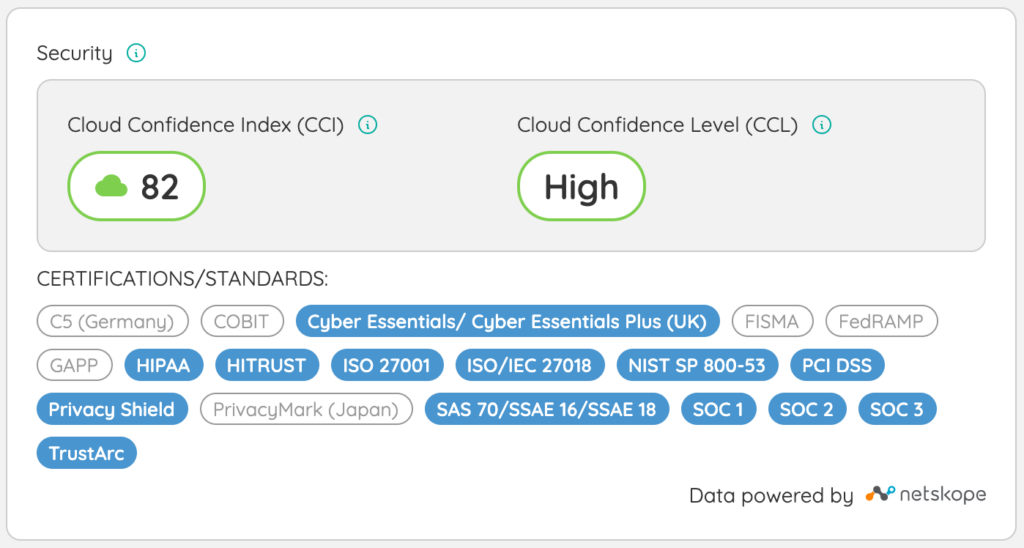
Zylo surfaces Netskope’s Cloud Confidence Index and Cloud Confidence Level. With this data at your fingertips, you can:
- Understand if your shadow IT applications meet security and compliance requirements.
- Prepare for security audits, like SOC 2, and identify applications that are not compliant.
- Ensure your SaaS applications meet regional standards and requirements. For example, if you do business in Europe, you need to know which applications are and are not GDPR compliant.
Going beyond Security
In addition to driving a more secure SaaS stack, these security details further empower IT and Procurement teams to make better business decisions regarding their SaaS investments.
Inform Upcoming Renewals
For Procurement, security information is especially helpful when preparing for upcoming renewals. Procurement teams can look at risk scores of renewing applications, alongside the certifications your team has deemed important to the business.
Risk is an important variable that can determine whether an app should be renewed or potentially sunset in favor of a more secure alternative. Additionally, if an app’s risk score has changed over time, Procurement teams can initiative a security review or potentially leverage risk information as part of their negotiation strategy.
Consolidate Redundant Applications
For IT teams that are comparing applications to consolidate their SaaS portfolios and reduce redundancies can now leverage security information in their rationalization efforts.
With App Compare, you can compare security risk scores of multiple apps side-by-side and even bring other details – such as app usage and spend – for a complete picture of your stack.
For example, let’s say you are comparing three project management tools. They all have similar usage and spend, but have widely different CCI scores of 50, 79 and 15. There might be a good case to cancel the application with the lowest risk score (15) l) and consolidate your portfolio.
Mitigate SaaS Risks with Zylo’s Security Detail
Visibility into security and compliance information and understanding the risk associated with your SaaS environment is essential to managing risk. Zylo’s Security Details provides instant visibility into SaaS attestations and certifications for the SaaS tools your teams rely on.
With this insight, IT and Information Security teams can quickly spot applications that pose a security risk to the business. Request a demo to see how Zylo can help keep your business safe and make confident renewal and purchase decisions.
ABOUT THE AUTHOR

Thom McCorkle
As Zylo's Director of Product Marketing, Thom is responsible for leading Zylo's product marketing strategy and execution with a passion for aligning customer needs and Zylo's value into everything we build and launch. He brings 7+ years of experience working with Zylo's customers and prospects with various roles from leading Customer Success to enablement and sales/solution strategy.