
5 Industry Experts Weigh In on the 2026 SaaS Management Index
Table of Contents ToggleWhat Is Shadow IT?What are the Sources of...
Back
Back
Search for Keywords...
Blog

Table of Contents
With SaaS, the Pareto principle – the idea that 80% of consequences come from 20% of actions – also applies to IT. A majority of SaaS-related problems usually stem from a minority of IT spend. It’s one of the issues presented by shadow IT (software and services outside of direct IT control). As companies adopt more SaaS applications to equip their workforce for productivity, IT is often left scrambling to keep up.
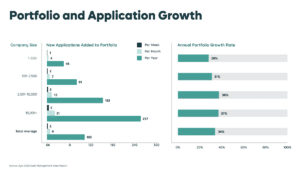
With organizations adopting an average of seven new SaaS applications each month, it’s no surprise that shadow IT is growing rather than shrinking within most companies today. In fact, those new apps add up to 33% portfolio growth annually.
What can we do about it?
Based on a review of more than $40B in active SaaS spending under management, Zylo recently released its annual SaaS Management Index report. As part of the data analysis, Zylo examined anonymized employee expense spending at hundreds of businesses that use Zylo’s SaaS management platform.
By analyzing the expense and reimbursement line of supplier spend, Zylo identified three of the most common types of applications that exist as shadow IT.
To start, shadow IT might not be quite as nefarious as it sounds. “Shadow IT refers to IT devices, software and services outside the ownership or control of IT organizations,” according to Gartner’s straightforward definition.
Shadow IT includes everything from SaaS applications sourced by a fast-moving GTM team to individual licenses adopted (and then expensed) by individual employees. In a phrase, shadow IT refers in part to SaaS applications that somebody knows something about — it’s just not consolidated and centrally controlled by IT.
Some of the challenges associated with shadow IT include:
SaaS applications are meant to make it easier for teams and employees to adopt new tools for productivity, collaboration, and training. But this can have a downside: employee expense spending is a notable source of shadow IT.
According to our benchmark data, today IT controls just 26% of all SaaS spending in the typical company — but directly manages only 16% of SaaS applications.
Business units (that is, teams working and iterating to quickly solve problems) control more IT spend and individual employees account for more SaaS applications.
The result is more decentralized management of SaaS applications — and more shadow IT over time.
The average company now maintains 275 SaaS applications. Employees expensing SaaS applications is a particularly notable contribution to the problem: this purchasing approach accounts for just 3.8% of SaaS spend but represents more than one-third of SaaS inventory in the average organization.
Which kinds of applications are the biggest sources of shadow IT? Entire teams are now empowered through SaaS collaboration, training, and web conferencing applications. But these applications have also become some of the biggest sources of shadow IT.
Common products: Asana, Slack, Jira, Airtable, Monday
What makes team collaboration applications a likely source of shadow IT?
The risks associated with team collaboration applications include:
Common products: Skilljar, Docebo, Cloud Academy
While the main issue in collaboration SaaS applications is the number of available tools, training software presents a different challenge for IT: these applications have a huge range of specific training functions. Sales, corporate training, security training, technical training — all present different requirements. It’s a broad category that can be difficult to effectively manage.
The risks associated with training applications include:
Common products: Blue Jeans, Citrix GoToMeeting, Zoom
RELATED: ComputerWorld: How ViacomCBS Cut Zoom Costs, Not Jobs
You can’t solve a problem until you know where the biggest issues lie.
The first step to “solving” shadow IT is SaaS discovery. That means uncovering how you’re spending, where you’re spending, and how much you’re spending across the entire organization — whether the SaaS applications are sourced by IT, by business units, or by individual employees.
Use a SaaS management platform (like Zylo) to help your organization discover shadow IT, and optimize applications by:
Shadow IT is not something that can be eliminated entirely. At the same time, shadow IT presents increased risk for the company — both in terms of finance and security. Getting a handle on all of your SaaS licenses (and spend) will lay the foundation for more purposeful spending and a more secure employee stack.
Ready to start addressing your shadow IT? Request a demo of Zylo today.

Table of Contents ToggleWhat Is Shadow IT?What are the Sources of...

Table of Contents ToggleWhat Is SaaS Compliance?Why SaaS Compliance MattersKey Types...

Table of Contents ToggleWhat Is Shadow IT?What are the Sources of...

Table of Contents ToggleWhat Is Shadow IT?What are the Sources of...
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |