
David Stoicescu: More SaaS, More Information Security Problems
Table of Contents ToggleEpisode SummaryGuest SpotlightEpisode HighlightsSaaS Management is a Team...
Back
Back
Search for Keywords...
Blog

10/24/2023
Table of Contents
IT teams of modern enterprises today have an opportunity to serve as champions to their internal customers.
The reality of today’s workplace is that people have access to more tools than ever before to help them do their job more effectively and efficiently. And they can work from wherever they need to be and with whatever device may be at hand.
That flexibility is great for productivity. But it does mean that IT, cybersecurity, and finance teams must create foundational pillars to enable this without putting the enterprise under more stress or risk of a malicious or inadvertent breach or loss of data, let alone inefficient spending.
Netskope believes that with a Zero Trust IT infrastructure built in the cloud, for the cloud, it can deliver performance and security for users. But even better, it can deliver the visibility and enforcement tools to continuously enable customers to safely enable their users to do their jobs.
How you may ask? By deeply understanding what activities users engage in, with what data, in which applications (private or public). Netskope can uncover the scope of the actual IT infrastructure employees and contractors have “stood up” and potentially populated with sensitive data, without formal IT onboarding.
Netskope can correlate this to millions of websites, thousands of private applications, and over 70,000 SaaS applications. In the last case, the Netskope Cloud Confidence Index (CCI) continuously compiles millions of pieces of information around the security posture and data management of all of those SaaS applications. This enables customers to make informed security decisions about what trusted activities to allow users to perform with each.
For example, a user attempting to use zippyshare (or Evernote, etc.) could be presented with a coaching page, informing them that the company’s official online storage and sharing solution is Microsoft OneDrive. Then, they’d be redirected to a link to open an IT request for consideration of their app of choice.
With Netskope’s integration with Zylo, customers are now able to see the CCI data of every SaaS application that their users leverage. It enables the finance department to understand the impact of individual buying decisions into potentially duplicative, unapproved, unnecessarily expensive, or fundamentally less trustworthy applications.
Now when an employee or department decides to use a credit card to procure licenses to an application IT didn’t know about and vet, and that Finance doesn’t have a pre-negotiated contract price for, the Zylo platform alerts them to this shadow IT usage.
The unknown is now known, and its impact can be quantified and reduced – thanks to Zylo Security Detail powered by Netskope.
Longer term, Netskope customers will be able to take advantage of information from Zylo by updating their own CCI database with information about the officially onboarded applications Zylo monitors. Doing so can help Security teams construct better enforcement policies.
Now the Cybersecurity team can be in lockstep with Finance and IT, ensuring that the right steps are taken to leverage a 360 degree view for appropriately enabling the users to be safe, efficient, and productive. You can hear me share more about the vision of this partnership in this on-demand webinar.
I’m very excited about this integration as it brings about the power of the ecosystem for sharing key context to drive zero trust architectures based on many different views of “risk.” To learn more about the future of Zylo and Netskope’s partnership, contact your account teams.
ABOUT THE AUTHOR

David Willis
David is an experienced business, security, and technology leader with over 20 years of experience across telecommunications, financial services, and software industry verticals. Today, he serves as the VP of Technology Integrations at Netskope, a recognized security leader.

Table of Contents ToggleEpisode SummaryGuest SpotlightEpisode HighlightsSaaS Management is a Team...

Table of Contents Toggle3 Key AI Risks for SaaS ManagementRisk #1:...
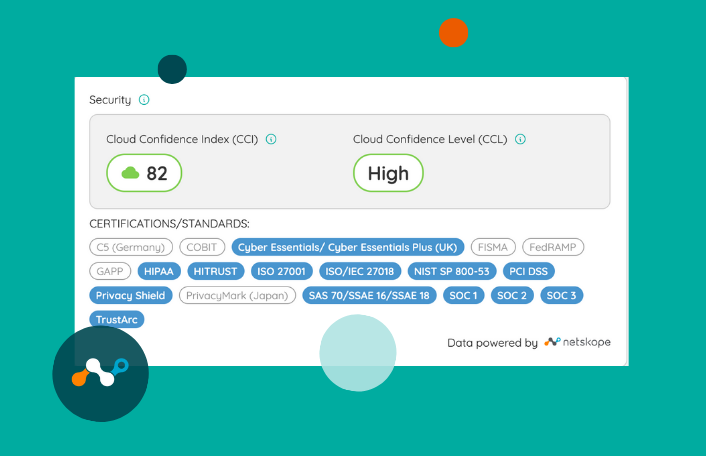
Table of Contents ToggleWhy Visibility Is Essential to Keeping Your Business...

Table of Contents ToggleDelivering Performance and SecurityEasily Assess Security Risks with...
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |