Table of Contents
On-premises software solutions no longer meet the needs of today’s digital-first organizations. Cloud applications, or SaaS, provide the convenience, affordability, and flexibility required to power companies of all sizes, whether employees work in the office, from home, or a hybrid of the two.
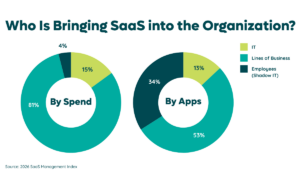
While the ease of SaaS acquisition helps companies stay agile, it also leads to less IT oversight. According to our 2025 SaaS Management Index, IT controls only 26% of SaaS spend and directly manages 16% of the average organization’s SaaS applications.
That means 84% of the apps entering your environment via employees and lines of business are likely unvetted. And they’re often riskier. Our data shows that 60.8% of expensed software have “Low” or “Poor” security risk scores.
On top of that, only 21% of an organization’s applications, on average, are secured behind single sign-on. Combined, these stats depict an environment full of cybersecurity gaps that open the door to tremendous risk if not addressed.
Learn more about the cybersecurity risks SaaS poses and how to address them in this Q&A with Zylo’s Director of Security, Daven Combs.
Exposing and Resolving Cybersecurity Gaps: Q&A with Daven Combs
With 20+ years of experience, Daven Combs has watched the shift from on-premise software to SaaS, and shares his best tips and practices for this new age of software acquisition.
What makes SaaS a cybersecurity risk?
SaaS enters and exits organizations at a rapid pace. Any employee with a company credit card has the ability to purchase new applications, and it’s safe to say most employees don’t actually read what they agree to before hitting “buy.”
Every time you log into Zylo, you’re probably going to find a new tool you didn’t know your company had. Or worse, if you don’t have a SaaS Management Platform like Zylo, you won’t discover those new applications.
What kinds of cybersecurity risks can impact an organization?
Each new application could be a pathway for someone to find out more information about your company, which can result in social engineering (baiting, phishing, etc.), or even a breach. The financial and reputational impact of data breaches follow your company for a long time.
You also encounter compliance risks when PII (personal identifiable information) is stored within applications. Not to mention regulations like the European Union’s General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), and the Health Insurance Portability and Accountability Act (HIPAA) mandate wide-ranging implications for the use of, storing, and transferring of consumer data and privacy.
How does a SaaS Management Platform proactively mitigate cybersecurity gaps?
Information is key to knowing what’s happening in your organization. When you hear about a vulnerability in the industry in one application or across several, visibility into whether your company uses those tools allows you to act quickly. If you find your company uses a vulnerable software, you should then track down who owns it, what they use it for, and what information is stored within the application.
Zylo’s service team helps customers proactively categorize and tag SaaS to know which applications contain PII or PCI. Knowledge of which applications are the most vulnerable helps IT managers remain vigilant. And when someone in your organization downloads a new software application, Zylo notifies you immediately.

What’s the next step once you’ve identified cybersecurity gaps?
Organizations need to establish a process for identifying, monitoring, and mitigating cybersecurity gaps. The lack of a process itself poses a risk.
The weakest link in any company is not the lock you put on the door or the badge you make staff wear—it’s the employees and their behavior. Employees must be trained to understand security risks, how to avoid them, and how to report them. Employees need to understand that the liability sits with them if they see a security gap and ignore it.
When a risk or security gap surfaces, IT professionals need to catalog it. For lower-level risks—depending on the company’s risk tolerance—cataloging may be enough. You don’t need to inform executives or the board.
Escalate higher-level risks to leadership. From there, leadership needs to figure out how the risk occurred and either continue using the software while accepting the risk or evaluate whether to eliminate the software entirely. This must be weighed with all the other risks the company currently faces. If they choose to accept the risk, the liability of the decision then lies with them.
What process should be in place for SaaS acquisition?
Consider a freedom within a framework model, which allows employees to self-select their tools from a curated library of vetted and approved software. Anything outside of the catalog would need to go under review before the employee downloads it.
Next, IT needs a process for review. First, ask how the software is going to be used. This helps assess the level of risk. For example, an application used to store customer data needs security professionals to touch every bell and whistle and flip all the switches to ensure it’s secure. For a design tool used to capture an image or make a simple graphic, you don’t need to throw it through the security wringer. That’s how you lose adoption to security.
Train people on this process when they onboard, but also follow an offboarding process to deprovision an employee’s applications and services when they leave the company.
Evolving Your SaaS Governance Framework for the Digital Workplace
Learn MoreWhat should a company look for in a SaaS Management Platform?
Your SaaS Management Platform needs to offer robust discovery insights to identify all applications within a platform, provide usage data, and drill down deeper to uncover license and payment information. It enables effective SaaS inventory management.
You should also look for a SOC 2-compliant tool. SOC 2 refers to security guidelines designed for service providers who store customer data. This certification, which Zylo achieved (SOC 2 Type II, specifically) with zero exceptions, ensures the management platform you entrust with your SaaS has proper security practices in place and keeps up to date on the everchanging industry requirements.
Business owners and IT professionals don’t have time to track down every application within their organization to find cybersecurity gaps and vulnerabilities. When it comes down to it, what companies need is a solution to provide complete SaaS visibility.
Learn how the Zylo Discovery Engine uncovers all SaaS with nearly 100% accuracy.
How the Zylo Discovery Engine Powers the Most Comprehensive SaaS Management Platform
Learn More