
Risk 101: Don’t Get Caught with Cybersecurity Gaps
Table of Contents ToggleWhat Is Single Sign-On?Benefits of Single Sign-On Beyond...
Back
Back
Search for Keywords...
Blog

Table of Contents
Securing sensitive information has never been more critical, as data breaches are frequent and increasingly costly. The average cost of a data breach in the U.S. has soared to $4.45 million — a 15% increase over the past three years, as reported by the IBM 2023 Cost of a Data Breach Report.
Despite these alarming statistics, a surprising finding from Zylo shows that, on average, only 21% of applications are protected by single sign-on (SSO) solutions. With 82% of IT and Security Asset Management (SAM) professionals identifying the reduction of security risks as a top priority for 2024, the need to extend SSO coverage across more applications has become more pressing.
In this blog, we’ll cover why single sign-on is important for security and how to get more applications secured behind SSO.
Single Sign-On (SSO) is an authentication service that allows users to access multiple applications with a single set of credentials. It ensures that an end user is who they say they are, and the device connecting to an application meets security requirements prior to providing access. Often, the service providing the SSO is enabled with additional capabilities, such as multi-factor authentication, IP Passlisting, managed device verification, and baseline security assessment checks.
Single Sign-On (SSO) is an integral component of Identity and Access Management (IAM), which includes the tools and policies for managing user identities in an organization. SSO integration into IAM improves security and operational efficiency by enabling centralized management of user identities and credentials. This allows IT departments to effectively control access to data and ensuring compliance with regulatory standards.
While security is often the first thing that comes to mind regarding single sign-on, it can also streamline the user experience, create efficiencies for IT, and help your organization scale. Let’s dive into each of the benefits.
SSO simplifies the user experience by reducing password fatigue. Users no longer need to remember multiple passwords, leading to increased productivity and user satisfaction.
It centralizes the authentication process at a single point, typically managed by a dedicated identity provider (IdP). This IdP acts as the trusted authority to authenticate users and issue tokens that systems recognize.
While there are single sign-on security risks, such as giving a single hacked password the ability to open multiple apps, the benefits generally outweigh the risks.
IAM frameworks enhance your ability to comply with regulations concerning data protection and privacy. That’s because SSO solutions often come with robust auditing and reporting tools. By reducing the number of times a user must enter their credentials, SSO minimizes the risk of phishing and other forms of security threats. In addition, SSO minimizes IT overhead associated with password resets, user account management, and dealing with access issues.
As your organization grows, managing more user identities becomes more complex. SSO plays a pivotal role in IAM by scaling efficiently as new users and services are added. Integrating SSO within an IAM strategy tightens security, improves operational efficiency, enhances compliance capabilities, and provides a better user experience.
Today, organizations use various SaaS applications to improve business operations and productivity. Ensuring the security of these applications requires proper management and monitoring, starting with a thorough understanding of your SaaS inventory.
Decentralized SaaS procurement makes visibility a challenge, with 83% of applications today purchased outside of IT. When it comes to security, this leads to blind spots for your IT and InfoSec teams. If you’re only focused on the IT-owned apps, there are likely hundreds of applications that you don’t know about and are sitting around unmanaged. Especially those pesky shadow IT apps.
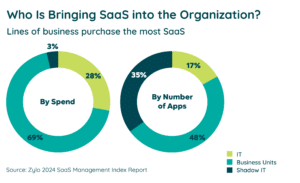 With ongoing discovery and centralizing your SaaS inventory—also known as SaaS inventory management—you can eliminate those blind spots.
With ongoing discovery and centralizing your SaaS inventory—also known as SaaS inventory management—you can eliminate those blind spots.
The dynamic nature of technology and business means new software can be introduced at any time. In fact, organizations see an average of six new apps entering the environment every month. Continuous discovery of SaaS applications is critical to maintaining security and governance.
 With continuous monitoring, Zylo’s Discovery Engine can automatically detect and inventory all SaaS applications being accessed across your organization. It relies on AI and machine learning with a focus on financial discovery to achieve this. In addition, your software inventory is updated in real time, ensuring that you immediately see any new applications or changes.
With continuous monitoring, Zylo’s Discovery Engine can automatically detect and inventory all SaaS applications being accessed across your organization. It relies on AI and machine learning with a focus on financial discovery to achieve this. In addition, your software inventory is updated in real time, ensuring that you immediately see any new applications or changes.
Taking that a step further, Zylo gives you line of sight to new software acquisitions. For instance, your team gets notified when a new purchase is made, whether expensed or directly purchased, effectively managing shadow IT. This is crucial in closing the security gaps that unauthorized software might introduce into the organization’s ecosystem.
How the Zylo Discovery Engine Powers the Most Comprehensive SaaS Management Platform
Learn MoreOnce you have visibility into all your applications, you’ll want to know which are SSO capable but not yet configured. Zylo does this for you automatically, being tracked as a key data point in your SaaS inventory.
You’ll also want to know your company policies, compliance, and contractual requirements regarding access and passwords, and identify any specific statements regarding SSO.
Once you have that information, sort the applications based on factors important to your business. Here are a few examples:
Once you have your prioritized list, begin assessing each app. You’ll want to understand if it is technically and finanically possible to enable SSO.
Cost Considerations
Many applications only allow for configuring advanced authentication methods from behind an Enterprise level licensing of their product.
If your application use case does not warrant the cost of purchasing an Enterprise license tier, it may not be viable. In this scenario, be sure to follow any of your company’s risk management exception processes if the application would otherwise violate a compliance or policy commitment.
If the business is not willing to accept the associated risk, you may be required to purchase the Enterprise license tier so that you can use SSO.
Technical Considerations
If it is functionally possible to use SSO, then you can move forward configuring it for your applications.
To enforce SSO, be sure to disable all other forms of authentication. Other authentication methods are typically not as secure, meaning you lack centralized visibility into logging, monitoring, and auditing who is accessing your applications.
In some cases, the cost or technical capability of configuring SSO with your primary identity provider may not be feasible. If so, you can also use other tools with centralized authentication capabilities.
It is nearly as secure to enforce such authentication methods as the only or required method for access, such as configuring Google Workspace, Azure, or Github Authentication to authenticate with your identity provider (e.g. Okta).
As cyber threats evolve, so too must our security methods. With a majority of applications not enabled for SSO today, it’s a missed opportunity to improve security. Using a SaaS Management platform like Zylo can help you identify blind spots and inform creating and implementing your SSO roadmap.
Learn how ongoing SaaS visibility and inventory management with Zylo can help. Or, request a demo to see it in action.

Table of Contents ToggleWhat Is Single Sign-On?Benefits of Single Sign-On Beyond...

Table of Contents ToggleWhat Is Single Sign-On?Benefits of Single Sign-On Beyond...

Table of Contents ToggleWhat Are the Risks of Improper SaaS Offboarding?5...

Table of Contents ToggleStreamlining the Vendor Procurement Process and Gaining VisibilityUnderstanding...
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |
