
FinOps Software Explained: Benefits, Tools & Key Features
Table of Contents ToggleWhat FinOps Means in the Modern Cloud EnvironmentWhy...
Back
Back
Search for Keywords...
Blog

Table of Contents
In the world of SaaS, IT is no longer the sole buyer. Employees can purchase SaaS—and do so as easily as entering their credit card number. Today, 6.6% of employees expense software purchases. While that’s a 67% decrease from 2022, it’s still significant and poses problems for an organization.
Shadow IT—the use of unauthorized or unmanaged SaaS applications—is a source of uncontrolled spend, SaaS sprawl, and security risks. In fact, 60.8% of expensed apps have “Poor” or “Low” security ratings via Netskope’s Cloud Confidence Index™. Expensed apps also result in nearly half a million dollars in costs per year on average per company. This spending makes up only 1% of total SaaS spending but still accounts for 45% of applications.
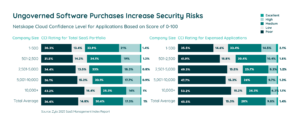
These applications offer convenience, flexibility, and cost-effectiveness, making them an attractive choice for employees. However, the risks of shadow IT have become a significant concern for organizations.
(by transaction volume)
Today, AI increasingly fuels employee app preferences. Last year, for the first time since Zylo started tracking this data, AI apps appeared on the list of most expensed apps. In 2024, ChatGPT landed the #2 spot, a jump from #14 in 2023.
As if managing hidden costs and risks of shadow IT weren’t hard enough, AI adds new complexities. How do you keep tabs on consumption? How do you budget appropriately? How is your data used and stored by the vendor?
Whether a regular old SaaS app or an AI-native app, you need to bring unknown expense purchases to light. While apps differ from company to company, let’s look at the ones that are most often expensed. The list below is based on Zylo’s 2025 SaaS Management Index report.
Employee software preferences continue to change. The only new app entering the Top 5 is ChatGPT, while CliftonStrengths fell from #3 to #5, allowing Canva and Kudoboard to jump ahead. And then there are apps that completely fell out of the top fifteen: Calendly, Adobe Creative Cloud, and MasterClass.
Here’s a breakdown of the five most expensed apps in 2024.
As we mentioned, AI tools showed up on our most expensed apps list for the first time in 2023. It’s safe to say that they solidified their spot going into 2025.
Specifically, ChatGPT and OpenAI API are the most popular AI-native apps—those with a core focus and designed specifically with artificial intelligence. But AI-powered features are also increasingly integrated into many of these expensed apps, such as Grammarly and Canva. This trend is not going away.
 Our data shows leading indicators that AI apps are poised for growth. We found that in 2024, spending on AI-native applications rose 75%, with the highest spend on OpenAI API, Microsoft 365 Copilot, Glean, Weights & Balances, and ChatGPT.
Our data shows leading indicators that AI apps are poised for growth. We found that in 2024, spending on AI-native applications rose 75%, with the highest spend on OpenAI API, Microsoft 365 Copilot, Glean, Weights & Balances, and ChatGPT.
While helpful for productivity and innovation, the unauthorized use of AI apps can lead to hidden costs and potential security risks for the organization. The unmanaged use of AI tools can lead to hidden costs, such as subscription fees or API usage charges. Additionally, using ChatGPT may introduce security risks, as employees may inadvertently share sensitive information with the tool or expose the company to potential data breaches.
Of the IT leaders we surveyed, nine in ten (89.4%) have concerns about the security risks associated with AI tools. In addition to staying on top of expensed apps (shadow IT), education on proper use of these tools and enforcement of governance policies will be critical for mitigating these risks.

For more data like these, check out our list of 111 unmissable SaaS stats, or download our SaaS Management Index.
At Zylo, we believe effective SaaS Management requires continual discovery, active monitoring, and identification of all new SaaS expense purchases. Check out some ways to create a cloud governance framework and prevent expensed SaaS applications from costing your organization.
To mitigate these risks and better manage your SaaS stack, you must start with SaaS discovery. That means getting visibility into all the applications in your environment.:
How the Zylo Discovery Engine Powers the Most Comprehensive SaaS Management Platform
Learn MoreToday’s workers increasingly value flexibility. Allowing them to easily discover and select their preferred tools raises awareness of what software is available, increases utilization, and reduces shadow IT. Freedom within a Framework is a popular SaaS governance strategy that puts guardrails in place without hindering employee productivity. It sits between centralized and decentralized governance.
It starts by creating policies to curb rogue software purchases. Often that involves putting restrictions on expense purchases – either setting a dollar threshold for what may be expensed or banning them altogether. The route you choose depends on what makes sense for your business.
 While policies get you off to a strong start, the key is in enforcing them. Visibility and education are key to making sure your policies work.
While policies get you off to a strong start, the key is in enforcing them. Visibility and education are key to making sure your policies work.
Offering employees an enterprise software store or application catalog helps them see what apps are available to them. Typically, the apps in your catalog are vetted and standardized software titles. If a tool is not listed, you can then provide guidance on how to properly request new purchases.
Education is also critical to enforcing governance. For instance, employees need to understand why you’ve taken this stance on software purchasing and usage. Help them understand the potential risks and costs associated with unauthorized app usage, and encourage the use of approved tools and platforms.
By addressing the underlying causes of shadow IT, businesses can ensure better control over their SaaS portfolio and maintain a secure and efficient IT environment.
Evolving Your SaaS Governance Framework for the Digital Workplace
Learn MoreFor many organizations, introducing more rigid governance around SaaS acquisition can keep expense spending in check. Your software approval process can be as simple as a quick form submission to request a new application.
Or, it can be as comprehensive as a software review board, involving a cross-collaborative team to review each new application request (e.g., Procurement, IT, Legal, and Accounting). While a review board may slow down the acquisition process and restrict who can acquire software, many Zylo customers say it effectively reduces shadow IT and expense spending.
Once you have governance in place, you can begin to eliminate shadow IT.
Start by identifying which apps you already have an enterprise agreement for. Then, check if licenses are available and migrate the user or users under that contract. Before canceling the other subscription, understand the terms and when you’re able to pull the plug.
If you don’t already have an enterprise agreement, notify end users they’ve purchased outside of policy and request they cancel the subscriptions. Next, direct them to your application catalog to select an already approved tool. If they’re unable to find a tool they need, provide direction on how to request the purchase of a new tool if that fits their needs better.
At this point, you’ve done all this hard work, the last thing you want is for shadow IT to creep back into your environment. Make sure you have proper monitoring in place so you’re alerted when a new app or payment comes in that is against your policies. Then you can take quick action, whether asking to cancel the subscription or not reimbursing them on future payments.
The rise of shadow IT and the increasing use of expensed SaaS applications highlight the need for organizations to gain a comprehensive understanding of their SaaS landscape. Your organization can better manage its SaaS stack, control spending, and improve overall security by addressing the hidden costs and risks associated with these applications. You can start achieving these goals by following the steps outlined in this article.
Do you know your organization’s most expensed SaaS applications? Employees expensing SaaS leads to shadow IT. Luckily, Zylo’s AI- and Machine Learning-powered Discovery Engine is unmatched at finding 100% of your SaaS — even those expensed apps hiding in the shadows. Schedule a demo and see how Zylo can go to work for you!

Table of Contents ToggleWhat FinOps Means in the Modern Cloud EnvironmentWhy...

Table of Contents ToggleTop 15 Most Expensed Apps for 2024What Can...

Table of Contents ToggleTop 15 Most Expensed Apps for 2024What Can...

Table of Contents ToggleKey Themes That Shaped SaaS Management in 20251....
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |
