
From Chaos to Control: Applying FinOps Thinking to SaaS
Table of Contents ToggleWhat Is Shadow IT?Visibility: The Biggest Barrier to...
Back
Back
Search for Keywords...
Blog

Table of Contents
Shadow IT refers to the unsanctioned use of IT devices, software, applications, and services outside the ownership or control of IT. Some organizations embrace it while others despise it. If you fit into the latter category, the question often remains: how do we eliminate shadow IT? Before getting into the ‘how’, it’s important to understand why it happens in the first place.
Shadow IT (as well as shadow AI) is just another way of saying applications bought by employees. Often, these employee-led purchases are made on a credit card and expensed. Our data shows a significant portion of your stack are apps purchased by individuals. In fact, they comprise 35% of your stack. So, why are they circumventing purchasing policies or “going rogue”?
“Someone’s spinning up some SaaS tool and it ends up being shadow IT. It’s not malicious. It’s someone trying to solve a problem.”
— Brad Pollard, CIO
Shadow IT spawned from the ambitious drive for efficiency, convenience, and innovation. It appears like a beacon of agility in an otherwise bureaucratic IT environment. While employees are well-intentioned, there are hazards that go undetected.
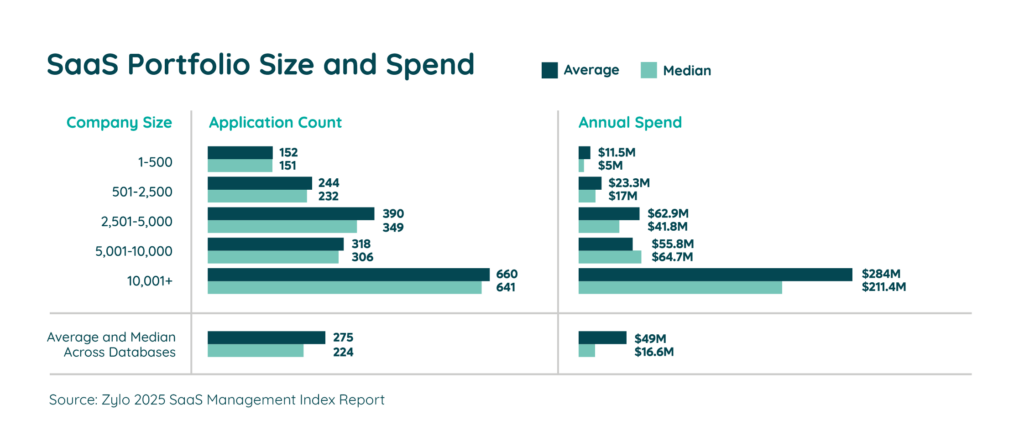
The cost of shadow IT applications is often the first risk companies think of and address. On average, companies spend $49M a year on SaaS and employee SaaS purchases make up 3.6%. Compare that to 2022 where shadow IT comprised 7% of total SaaS spend. While only a small portion of your total spend, it can quickly add up depending on the size of your organization.
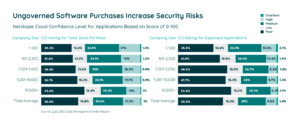
Even scarier are the potential vulnerabilities these applications bring into the business. In many cases, shadow IT and shadow AI tools do not meet the standards set by IT departments. They’re often hidden from enterprise security systems, putting the entire company’s data at risk. Our research shows that 60.8% of expensed software have “Poor” or “Low” security risks scores, as measured by Netskope’s Cloud Confidence Index.
 On top of that, shadow IT creates inefficiencies. Since IT doesn’t know about these apps, they’re often not behind single sign-on and aren’t connected to other systems. Redundancy often runs rampant, with duplicate apps and users with access to multiple apps that do the same thing. Employees’ search for productivity backfires, forcing data and collaboration to occur in silos. With AI tools added to the mix, it creates another layer of complexity to data security.
On top of that, shadow IT creates inefficiencies. Since IT doesn’t know about these apps, they’re often not behind single sign-on and aren’t connected to other systems. Redundancy often runs rampant, with duplicate apps and users with access to multiple apps that do the same thing. Employees’ search for productivity backfires, forcing data and collaboration to occur in silos. With AI tools added to the mix, it creates another layer of complexity to data security.
Despite even the best efforts, there’s no full-proof way to get rid of all the shadow IT in your stack. That’s because SaaS is ever-changing. In fact, organizations average six new applications entering their environment each month. But, there’s still hope.
Eliminating shadow IT requires a concerted effort and a judicious blend of policy enforcement, employee education, and embracing innovative IT solutions to effectively deal with shadow IT. In short: SaaS governance.
According to IDC, in the US, 70% of cloud application spending comes from line of business budgets – not IT. Even our own data shows this trend. When SaaS purchasing lacks governance, it frequently produces a proliferation of duplicate subscriptions, functional overlaps, and reduced utilization—which all lead to waste.
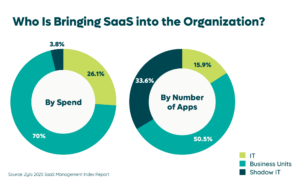 However, siloed departments and ineffective communications mean that visibility into your SaaS inventory is murky at best. Additionally, tracking your apps in a spreadsheet is timely and costly – and it does not perform SaaS discovery.
However, siloed departments and ineffective communications mean that visibility into your SaaS inventory is murky at best. Additionally, tracking your apps in a spreadsheet is timely and costly – and it does not perform SaaS discovery.
Many businesses have ditched the spreadsheet approach by deploying a SaaS Management Platform (SMP). That’s because discovery is the key tenet upon which it is based. For instance, Zylo’s Discovery Engine is known for finding 100% of your SaaS applications.
Not any type of discovery mechanism will be effective for eliminating shadow IT. Financial discovery is critical since shadow IT makes its way into the enterprise through expense channels.
It’s also important to note that finding shadow IT goes beyond pulling a report from your expense system. SaaS likes to hide. In fact, it’s notorious for flying under the radar as ambiguously named line items or miscategorized altogether. Zylo data shows that as much as 51% of software expenses are miscategorized. Surprisingly, we’ve found it under categories like Entertainment, Meals, and Office Supplies.
The Zylo SaaS Management Platform creates visibility in three ways:
By combining these viewpoints in a central system—also called SaaS inventory management—the platform provides comprehensive analytics to highlight redundancies and drive actionable insights.These insights often make the need for centralized governance more apparent.
Additionally, a SMP provides continuing oversight into cloud-based subscriptions, enabling IT leaders to set appropriate constraints for which SaaS applications need IT supervision. These thresholds are essential for developing more efficient management protocols that will optimize SaaS security and consumption.
How the Zylo Discovery Engine Powers the Most Comprehensive SaaS Management Platform
Learn MoreThe pervasiveness of shadow IT in organizations provokes significant concern for IT leaders. By circumventing approved channels, shadow IT presents a range of risks – from security vulnerabilities to regulatory compliance issues. Acknowledging these issues, a comprehensive strategy is necessary to curb the practice. Various mechanisms, such as policy changes, IT infrastructure improvements, and leveraging new technology like a SaaS Management Platform, can play a crucial role in successfully eliminating shadow IT.
Read on for three strategies to eliminate shadow IT or watch the video.
Business units create shadow IT and adopt SaaS applications to meet business goals. As a result, these buyers often overlook the risks of shadow IT. With this in mind, it’s important to note that best practices begin with the source: the SaaS buyer.
When IT builds relationships with SaaS buyers and understands their needs, they can help remove the obstacles and empower the business unit.
“It’s become so much easier to sign up for a service or software. Educating end users of the risks when they’re using software outside of whatever’s available within their company’s catalog is really important.”
— Shravya Ravi, Head of Software and IT Hardware Asset Management at LinkedIn
Through active collaboration, IT can work with business leaders to think like a CIO. That mindset enables them to identify and adopt the technology that will support business goals and enterprise-wide advancement. Collaboration also creates a framework for shared goals regarding SaaS application cost, value, and security.
The bedrock of eliminating shadow IT is SaaS governance. Establishing policies and procedures can mitigate the use of unsanctioned applications within the enterprise.
More and more, IT, Software Asset Management, and Procurement leaders are turning to a governance approach we like to call Freedom within a Framework. In short, it ensures the right controls are in place without stifling employees’ ability to get the tools they need to be productive and innovate.
When it comes to shadow IT, having an expense policy is a great starting point. For instance, AbbVie has put measures in place to reduce shadow IT and waste in its stack. Depending on your organization and culture, you may want to set:
Evolving Your SaaS Governance Framework for the Digital Workplace
Learn MoreAnother lever is to standardize your software catalog. Software standardization is a component of SaaS governance where you establish a catalog of preferred software for your business. Typically, it’s part of a broader, business-led initiative to standardize business processes and data across a large, global enterprise.
A software catalog helps employees understand what software is available and enable them to request new tools if they’re not there.
Beyond helping eliminate and prevent shadow IT, standardization also helps:
Adobe Drives Innovation and Massive Savings with Zylo
In the past 4 years, Adobe has rapidly scaled from $9B to $18B. This growth has made an already complex environment even more complex. Learn how they leveraged Zylo to get complete visibility into their SaaS portfolio, unlock millions in cost savings and avoidance and improve the employee experience.
Once you have complete visibility into your SaaS inventory and implemented governance, it’s time to take action.
Start by identifying which apps you already have an enterprise agreement for. Understand if licenses are available and migrate the user or users under that contract. Before canceling the other subscription, make sure you understand the terms and renewal date. That will be critical for knowing when you can pull the plug, so to speak.
What if you don’t already have an enterprise agreement? We recommend notifying end users that they’ve purchased software outside of policy. You should request that they cancel the subscriptions, or potentially risk not getting reimbursed on future payments. From there, you can direct them to your application catalog to select an already approved tool. Be sure to provide direction on the process they should follow to request the purchase of a new tool if that fits their needs better.
Once you’ve done all this hard work, the last thing you want is for shadow IT to creep back into your environment. That’s where monitoring comes in. Your SMP is a helpful tool here, as you can set up alerts for when new apps or payments enter the system. It becomes easy to flag those that are against policy. Then, you can take quick action to eliminate that shadow IT app.
Addressing and eliminating shadow IT can often be a source of quick wins for your SaaS Management program. If you’re trying to tame shadow IT, request a demo to see how Zylo can help you get started.

Table of Contents ToggleWhat Is Shadow IT?Visibility: The Biggest Barrier to...
Table of Contents ToggleWhy Data Integrity Breaks DownWhat Does Data Integrity...
Table of Contents ToggleWhat Is Shadow IT?Visibility: The Biggest Barrier to...

Table of Contents ToggleShelfware DefinedWhy Shelfware HappensPoor Organizational OversightShadow IT and...
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |
