
Understanding SaaS Procurement: A Complete Process & Best Practices
Table of Contents ToggleWhat Is SaaS Compliance Management?The Importance of SaaS...
Back
Back
Search for Keywords...
Blog

01/23/2026
Table of Contents
SaaS compliance management isn’t something you can put off until audit season. If your business runs on cloud apps, you’re already handling sensitive data through tools you don’t fully control. When you don’t know which apps store regulated information or who can access it, gaps build up quickly that are hard to unwind later.
In 2026, you need to show proof that your SaaS environment is governed and secure. Once you map the rules that apply to you, you can set controls that hold up under scrutiny. That also makes everyday work easier because you’re reducing risk while standardizing access and vendor oversight.
This guide breaks down what SaaS compliance management means, why it matters, and what to focus on first. After you understand the standards that may apply, you’ll know how to stay audit-ready while your SaaS footprint keeps evolving.
SaaS compliance management is the practice of ensuring every cloud application in your business aligns with regulatory requirements, industry standards, and internal policies. It plays a critical role in:
This practice is built on two essential capabilities: visibility and control.
With these foundations in place, teams can move from reactive problem-solving to proactive risk management.
SaaS compliance management strengthens your operational integrity. It enables you to:
Over time, effective SaaS compliance management supports a more secure, efficient, and scalable software ecosystem—designed to support business growth with confidence.
If you want compliance to support your business rather than slow it down, you need to understand where it delivers value. Your compliance processes can affect:
SaaS compliance management goes beyond meeting rules. It affects how customers view you, how regulators treat you, and how efficiently your teams can work when they rely on cloud software.
Customers expect you to protect their data. When your SaaS tools meet security and privacy standards, you earn the confidence required to maintain long-term relationships.
Building trust through compliance helps you:
When visibility and policies are lacking, small missteps can damage credibility. With compliance controls in place, you reduce the chance of incidents—and the cost of lost trust.
SaaS growth doesn’t exempt you from regulatory accountability. If your apps touch personal, financial, or health data, you’re responsible for compliance with all applicable laws.
Effective SaaS compliance management helps you:
The effort to stay compliant is far less costly than dealing with fines, litigation, or reputational fallout.
Compliance contributes directly to smoother operations. Standardized approval workflows and access controls reduce shadow IT, tighten governance, and eliminate manual risk.
Key benefits include:
By embedding controls upfront, you shift away from reactive security and enable more proactive risk management.
Compliance becomes a differentiator when prospects need proof of governance. It signals maturity, credibility, and trustworthiness—especially in industries where data handling is under scrutiny.
When SaaS compliance is built into your evaluation process, you gain:
Buyers want partners they can trust. Strong SaaS governance gives them confidence to choose you.
Strong compliance practices strengthens your resilience. If a vendor experiences an outage or data breach, you already know:
This preparedness reduces the impact of disruptions and accelerates recovery.
Over time, a governed SaaS environment delivers:
With risk under control, your team can plan and scale with confidence.
If you want SaaS compliance to actually hold up under scrutiny, you need to understand what makes it work in practice. The following components help you to see where gaps usually form and how to close them.
Every part of your SaaS environment touches data, access, money, or risk. Once you know which pieces matter most, you can focus your attention on the controls that protect you instead of spreading it thin across the wrong areas.
Data privacy defines how personal and regulated information is collected, stored, and shared across your SaaS tools. When customer, employee, or financial data flows through cloud apps, your organization becomes accountable for its protection.
Key aspects of data privacy in SaaS compliance management include:
Strong data privacy practices build trust and reduce the likelihood of violations or fines.
Data security ensures that information within your SaaS environment remains protected from breaches, leaks, and unauthorized access. Each SaaS application represents a potential risk surface if unmanaged.
SaaS compliance management in this context focuses on:
A secure SaaS environment strengthens your compliance posture and limits lateral risk exposure.
This dimension of SaaS compliance management connects your SaaS footprint to financial reporting standards and operational controls. Apps, subscriptions, and renewals have direct implications for compliance with accounting and internal audit requirements.
Financial compliance considerations include:
Clear connections between your SaaS usage and financial controls reduce audit risk and improve reporting accuracy.
Every SaaS provider contributes to your overall risk exposure. Their ability—or inability—to meet security and compliance standards directly affects your organization.
In SaaS compliance management, vendor risk is defined by:
Understanding your third-party risk profile is essential to managing shared accountability across the SaaS stack.
Identity and access governance defines who can use which SaaS applications and what permissions they hold. Without control, users can retain access beyond their role, creating unnecessary exposure.
This compliance category includes:
Effective governance reduces the risk of data misuse and supports role-based access enforcement.
Compliance in SaaS environments requires ongoing monitoring to remain effective. Cloud applications and user behavior change frequently. When you only check controls once a year, gaps have plenty of time to grow.
Key components of continuous governance include:
This ongoing visibility supports long-term audit readiness and reduces the risk of non-compliance.
License compliance ensures that your SaaS usage matches the terms of your contracts. Overuse can result in penalties, while underuse signals wasted investment.
Important elements of license compliance include:
Maintaining license alignment protects budgets and improves accuracy across software asset reporting.
Audit readiness is the ability to demonstrate compliance through centralized, accessible evidence. When documentation is dispersed or incomplete, SaaS audits become time-consuming and error-prone.
Key attributes of audit-ready environments include:
With proper evidence management, audits become a structured, predictable process. Audits go from a fire drill into a routine process you can handle with confidence.
The No-BS SaaS Management Playbook
If you want SaaS compliance to hold up under audits, customer reviews, and security questionnaires, you’ll need a shared blueprint for what “good” looks like. Here are the standards you need to know, especially if you operate globally:
Standards and frameworks help you define what to implement, what to test, and what to document. As you align your program to widely recognized frameworks, you’ll move faster on reviews because you’re answering questions with a consistent control story.
When selecting security frameworks, focus on those your customers and regulators already recognize. You can use them to shape control design, testing, and reporting. If you pick a framework your auditors know well, you’ll also reduce back-and-forth during evidence collection.
SOC 2 is an attestation report based on the AICPA Trust Services Criteria. Type I reports on design at a point in time. Type II reports on design and operating effectiveness over a period of time. Once you know which report your customers expect, you can align your evidence collection to that timeline.
The International Organization for Standardization and International Electrotechnical Commission (ISO/IEC) 27001 is a standard for building and running an information security management system (ISMS). After you adopt an ISMS approach, you’ll manage security as an ongoing system of policies, risk treatment, and continuous improvement rather than a one-time project.
The National Institute of Standards and Technology (NIST) Cybersecurity Framework is a cybersecurity outcomes framework you can use to organize your program. In CSF 2.0, outcomes are grouped into core functions that help you structure governance and operational security work. If you need a common language across security and leadership, CSF is often the easiest place to start.
The Federal Risk and Authorization Management Program (FedRAMP) is a U.S. government program that assesses, authorizes, and continuously monitors cloud services used by federal agencies. If you sell in the public sector, FedRAMP can become a gating requirement, so you’ll want to plan for formal assessment and ongoing monitoring.
Center for Internet Security (CIS) Benchmarks are prescriptive secure configuration recommendations for specific technologies. When you apply them, you’re typically hardening systems with documented baselines that you can validate through technical checks.
Once you handle personal data in SaaS, privacy compliance stops being a legal-only concern and becomes operational. You’ll need clear data flows, defined purposes for processing, and repeatable processes for rights requests. If you expand into new geographies, plan for privacy law overlap and conflicting timelines.
GDPR is the EU’s General Data Protection Regulation. If your business activities fall under GDPR, focus on:
California’s privacy regime includes the CCPA and amendments that expanded protections. If you do business with California consumers, you’ll need processes that support required disclosures and consumer rights requests. You’ll also want to account for rules around “sale” or “sharing” of personal information in certain contexts.
Brazil’s LGPD is a comprehensive data protection law with requirements around lawful bases, data subject rights, and governance expectations. After you map your processing activities in Brazil, you can typically reuse much of your GDPR-style operational approach, but you’ll still need to confirm local requirements.
PIPEDA is Canada’s federal private-sector privacy law for commercial activities. If you operate within its scope, you’ll need to manage consent and reasonable safeguards and handle access requests through a defined process.
Australia’s Privacy Act governs how covered entities handle personal information. If you become subject to it, you’ll need to align your collection, use, storage, and disclosure practices to the law’s requirements and related guidance.
Colorado’s privacy law applies to certain entities that process personal data of Colorado residents acting in an individual or household context. If you’re in scope, you’ll need mechanisms that support consumer rights and opt-out requirements where applicable.
The Virginia Consumer Data Protection Act (VCDPA) grants consumer rights and imposes obligations on controllers and processors subject to defined thresholds. After you confirm applicability, you’ll typically operationalize it through updated notices, request workflows, and vendor contract terms.
Connecticut’s law provides rights for residents and sets standards for controllers that process personal data. If you serve Connecticut consumers, you’ll want a repeatable way to classify data and respond to rights requests.
The Utah Consumer Privacy Act (UCPA) establishes consumer rights and business responsibilities under defined thresholds. Once you’re in scope, you’ll usually address it through privacy notices and operational request handling.
If you operate in certain heavily-regulated industries, you’ll often have baseline privacy and security obligations, plus additional sector-specific rules. When you’re planning SaaS compliance, you should treat industry regulations as design constraints for your product and your internal processes.
The Health Insurance Portability and Accountability Act (HIPAA) sets rules for protecting health information in the U.S. The HIPAA Security Rule focuses on safeguards for electronic protected health information. If you touch regulated health data, you’ll need the right administrative, physical, and technical controls, plus the right contractual structure.
The Payment Card Industry Data Security Standard (PCI DSS) defines security requirements for environments that store, process, or transmit payment account data. If your SaaS handles card data directly, you’ll need to carefully scope your cardholder data environment, then implement the required control set and validation approach.
Financial Industry Regulatory Authority (FINRA) expectations focus on how broker-dealers manage cybersecurity risk as part of broader supervision and risk management practices. The Gramm-Leach-Bliley Act (GLBA), through the Safeguards Rule, requires covered financial institutions to maintain an information security program designed to protect customer information. If you deal with any kind of financial services, you’ll often be asked to prove you can meet both operational security expectations and program-level governance requirements.
Family Educational Rights and Privacy Act (FERPA) protects the privacy of student education records at covered institutions. If your SaaS touches education records, you’ll need to align access, disclosure, and data-handling practices with FERPA obligations and the institution’s policies.
When SaaS systems impact financial reporting, compliance expectations shift toward control reliability and auditability. If you support finance workflows, revenue recognition, or financial processes, you should expect detailed evidence requests tied to control design and operating effectiveness.
System and Organization Controls 1 (SOC 1) reports cover controls at a service organization that are relevant to user entities’ internal control over financial reporting. If your SaaS feeds financial statements, customers may request SOC 1 evidence as part of their audit requirements.
System and Organization Controls 2 (SOC 2) may become necessary if customers often seek security assurance, even when the primary focus is on financial reporting. If you’re already producing SOC 2, you can reuse portions of your evidence, but you’ll still need to match requests to the right report type.
The Sarbanes-Oxley Act (SOX) drives internal control expectations for public companies, especially around financial reporting. If your SaaS supports SOX-scoped processes, customers may require stronger audit trails, more precise access controls, and more formal evidence of change management.
Accounting Standards Codification Topic 606 (ASC 606) and International Financial Reporting Standard 15 (IFRS 15) are revenue recognition standards that affect how subscription revenue is recognized. If your billing, contract, or provisioning data support revenue reporting, you need controls to ensure the data is complete and accurate.
Cloud compliance can fail fast when responsibilities are unclear. After you adopt cloud services, you still own key security and compliance obligations tied to your data, identities, and configurations. If you’re relying on vendor assurances, you’ll want to pair them with your own controls and validation.
Shared responsibility models define which security tasks are handled by the cloud provider and which ones remain yours. If you misunderstand the split, you can end up with gaps in identity protection, data security, or configuration controls. Once you document the split for each service model you use, you can assign owners and evidence collection more cleanly.
Cloud Security Alliance Security, Trust, Assurance, and Risk (CSA STAR) is a cloud assurance program with a public registry that documents security and privacy controls for cloud offerings. If you’re assessing vendors, STAR listings can help you compare control posture using a consistent reference point.
The following challenges can put pressure on security, finance, legal, and operational teams:
It’s difficult to keep compliance tight while your SaaS environment keeps expanding and evolving. Your portfolio can grow fast, span regions with different laws, and involve an ecosystem of vendors, users, and contracts that shift over time. Once you know the common challenges you’ll face, you can build repeatable processes and tooling support that help you stay ahead instead of scrambling after problems appear.
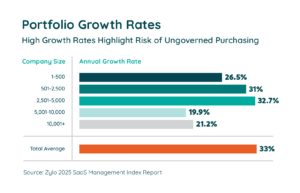
According to the 2025 SaaS Management Index, companies add an average of 7.6 new applications to their environments each month—or 33% portfolio growth. That pace makes is difficult to:
When you don’t automate discovery and governance, apps enter your stack without oversight. That increases shadow IT, multiplies unmanaged access points, and pushes audits farther out of reach.
Compliance doesn’t stop at one set of rules when your users and customers span countries or states. GDPR in Europe, CCPA/CPRA in California, and other privacy laws have different requirements for notice, consent, data retention, and rights requests. You need workflows for responding to requests that vary by jurisdiction. Unless you build a repeatable system, you’ll find yourself handling exceptions one at a time—indefinitely.
Every vendor you use—and every tool they integrate with—adds compliance risk. Third parties bring their own policies, security postures, and control gaps. If you don’t inventory and assess vendors continually, compliance gaps can hide in places you don’t expect, especially when tools share data or connect via APIs. That’s why you need continuous evaluation, not just point-in-time checklists.
Most teams don’t have the staff to keep pace with SaaS adoption and evolution. Security, compliance, and IT teams often juggle backlog work, audits, incident response, governance projects, and daily operations. Without automation support, manual processes quickly get overwhelmed. That means you end up reacting to issues instead of preventing them. Over time, that reactionary mode increases risk and reduces team morale.
Compliance must be ongoing. It starts when a tool is procured and continues through renewal or retirement. If you lack unified visibility across this lifecycle, you’ll miss:
Closing these visibility gaps gives you a real chance to stay ahead of compliance reviews instead of chasing evidence after the fact.
To keep SaaS compliance management consistent instead of episodic, you need practices that are repeatable and built into how you operate. Here are the core best practices that help you stay ahead:
Frameworks and policies only help when you pair them with visibility, evidence, and controls that you enforce over time. Once you select the right habits and tools, you’ll spend less time scrambling for evidence during audits and more time strengthening your compliance posture.
You need to know which rules actually apply before you spend time on compliance work. Start by mapping what kind of data you process. Then look at where your users and customers are located. After that, check whether your industry has any additional requirements. When those three inputs are clear, you can determine which regulations and standards you must follow.
According to Zylo data, organizations underestimate the number of apps they have by nearly 2X. When your SaaS tools spread across teams unknown to IT, risk grows quietly. To ensure visibility into usage, use a SaaS Management Platform (SMP).
An SMP will:
This doesn’t replace your compliance tools, but it does help you decide where to focus them.
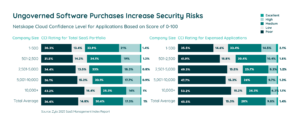
In the average portfolio, Zylo’s annual report found that 51% of applications have a “Poor” or “Low” risk score—based on Netskope’s Cloud Confidence Index (CCI). This means those apps may introduce significant security and compliance risks to your organization.
To understand where controls are missing or weak, conduct a gap assessment. Compare what you have today to what the relevant frameworks expect. Following with a risk assessment then helps you decide which gaps matter most to close. Together, these two assessments make it easier to prioritize fixes instead of trying to do everything at once.
Security controls reduce the chance that a compliance failure becomes a data breach. Once you know which apps handle sensitive data, you can enforce the proper protections. That includes access restrictions and authentication requirements. It also includes monitoring for unusual activity. These controls support frameworks such as SOC 2 and privacy laws by demonstrating that you are actively protecting data.
If you don’t document your compliance work, it’s almost impossible to prove it. Always record policies, risk assessments, and control testing. When you keep this information up to date, audits become much easier. You’re no longer trying to recreate decisions months later.
“The thing that auditors look for is if you have your processes documented… [In addition,] build a library of all your applications… You want to be able to adequately tell [auditors] with confidence, this is my list of certified applications.”
— Jennifer Clark, Global IT Asset Manager at Hyatt Corporation
Your vendors change over time, and their security posture can improve or decline. Their certifications can also expire. When you track those changes, you avoid being caught off guard by a third party’s weakness. SaaS management platforms help you manage vendors
by showing you vendor status and risk signals in one place.
Compliance only works when it runs continuously. Your SaaS environment changes as people join, leave, or adopt new tools. When you monitor those changes continuously, you catch problems early. That keeps your compliance posture from drifting out of alignment.
Automation helps you catch changes that can affect compliance before they become problems. Zylo supports this with automated alerts in two cases.
These alerts give you early warning signals, but they don’t fully replace a compliance platform. You still need a dedicated compliance tool to manage control testing, evidence, and audit workflows. When you pair Zylo with that tooling, you get visibility from Zylo and enforcement from your compliance system.
While AI-driven compliance platforms can help surface risk, you still need people to decide what action to take.
To keep compliance under control in a fast-moving SaaS environment, you need complete and ongoing visibility. You can’t protect data or enforce policy if you don’t know what is happening inside your stack. Once you bring everything into view, you can proactively manage compliance instead of reacting to issues after they occur.
Zylo helps by providing a single source of truth for your SaaS stack with key information that compliance teams need to stay audit ready:
If you want to stay audit-ready without slowing your business down, start by getting clear insight into what’s really in your SaaS stack. With Zylo, you can see where risk exists, respond to change as it happens, and support your compliance program as your SaaS footprint continues to grow. Request a demo today to see how it works!
ABOUT THE AUTHOR

Nicole Wood
Nicole Wood is the Senior Content Strategist at Zylo, where she develops content that educates and empowers enterprises to manage SaaS strategically. She is also the producer the Silver Stevie Award-winning podcast, SaaSMe Unfiltered.

Table of Contents ToggleWhat Is SaaS Compliance Management?The Importance of SaaS...

Table of Contents ToggleWhat Is a SaaS Savings Pipeline?Why Managing SaaS...

Table of Contents ToggleWhat FinOps Means in the Modern Cloud EnvironmentWhy...

Table of Contents ToggleWhat Is SaaS Compliance Management?The Importance of SaaS...
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |
