Table of Contents
There’s no doubt that cloud-based technology has changed the way we live and do business. However, it has brought a new generation of security risks. Back in 2017, an unnamed casino suffered a data breach – via its fish tank. The fish tank in question was wirelessly connected to the company’s temperature management system, and the unsecure connection allowed hackers in to steal several gigabytes of sensitive customer information.
But what does this have to do with SaaS? Well, without a proper security review, a SaaS application could well become your fish tank incident.
Security reviews ensure that applications meet your standards to protect both company and customer data.
Why You Shouldn’t Skip the Security Review
When we discuss security risks, we often turn to the financial impacts of a potential data breach. This is important, of course. However, there’s more to security than protecting revenue. Let’s take a look at why a security review is an essential step in SaaS acquisition and management.
Maintaining Security Policies
Consider the intended use, configuration, or capabilities of a SaaS solution. It’s possible they don’t meet your company’s security or associated policies. A review allows your security team to look into the use of a product and address potential violations.
Supporting Visibility
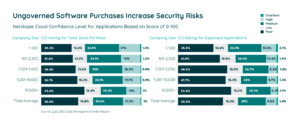
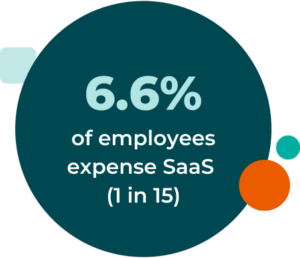
What’s more, your security team must be aware of all of the SaaS solutions in your environment at any given time.When you skip a review, don’t have visibility, and have misaligned leadership responsibility, it creates a triple whammy. Notably, leading to most shadow IT. You not only are unaware of these unsanctioned apps, but 60.8% of them carry higher risk. If one of these applications announces a security breach, the team needs to know. You also run the risk of missing security notifications if sole ownership sits with the employee. That’s whether they blatantly ignore a notification, or they leave the company. And you’re completely left in the dark.
Upholding B2B Agreements
When your company has another business as a customer, it’s likely you’re beholden to certain contracts or regulations. These agreements often include requirements to disclose what third parties you use to provide your services. Including your SaaS vendors. That means unknown SaaS applications in your environment could pose a breach of contract.
Recognizing Historical Risks
A security review will not only look into the tool itself but the history of the provider as well. If the solution has a history of security breaches or negative legal findings, that could indicate a potentially recurring problem. You’ll want to know if that risk is worth it.
Identifying Unknown Vulnerabilities
Validating SaaS Security Claims
SaaS vendors will often share their existing industry security certifications to help build a sense of trust. However, they may not be sharing the whole picture. A security review should include obtaining and reviewing relevant certification reports to ensure there are no findings or exceptions that your company would find unacceptable. At the least, you may find you need to ask more questions before signing a contract.
Evolving Your SaaS Governance Framework for the Digital Workplace
Learn MoreSteps in the Security Review Process
The exact steps you’ll need to follow for your own security review vary depend on your industry certifications, privacy requirements, and relevant laws dictating data security. It also depends on the data you supply to the SaaS company in question as well as your intended use of the application. However, the general areas your assessment should cover will include confidentiality, integrity, and availability.
What we will focus on here are the prerequisites and steps to follow when conducting security reviews for your SaaS applications.
Pre-Requisites before You Get Started
#1 Ensure Leadership Alignment on Risk Management
Before even considering how you would apply a security review process, your company must be aligned on risk management. Certainly, your Security team can surface what it believes is a risk to the company. Though, ultimately, the company and its leadership determine if those risks are acceptable, require a time-limited exception, or not acceptable and must be remediated or mitigated and reviewed again. In most scenarios, the Security team’s advice should be considered. But, they should not have the responsibility to decide on, or be held accountable for, how to handle most risk items.
That’s where risk management comes in. Your risk management program should be well established across your company’s leadership. The program helps eliminate arbitrary, unnecessary, or intangible claims and place liability of decisions around discovered risks into the hands of those now well informed decision makers.
#2 Determine Company-Wide Watermarks
Your company should determine the minimum security requirements you need from your SaaS vendors. These requirements vary from company to company, industry to industry. However, they establish a guideline to assess compliance according to those requirements.
For example, does your company or industry require SaaS providers to possess certain industry certifications or compliance with regulations such as the GDPR, SOC2 Type II certification, or PCI-DSS? Do they mandate security controls such as 2-factor authentication or IP Whitelisting to protect your data? And are those controls a must-have for your organization?
How about countries where the SaaS vendor and relevant third parties operate? Cybersecurity regulations vary across the world, and you should never continue with a SaaS vendor until you understand where they are located.
Knowing this information upfront will save time down the line.
Conducting Your Security Review
Once your team has decided to pursue a SaaS tool, it’s time to bring in the Security team. They conduct a high-level review of the solution for any immediate concerns or security gaps. Once it has cleared this review, as well as legal and finance, then it can be safely purchased.
Step 1: Request Security Documentation
Most SaaS sales teams are now practiced in the dance of security reviews. They’ve adopted many tools and processes for reasonably handling the upfront security and compliance needs to speed up the sales process. As a result, requesting a company’s Security “pack”, “package”, or “information” results in obtaining a significant amount of the evidence you will need to validate answers in the next step.
Step 2: Design a Standardized Vendor Security Questionnaire
When designing a security review questionnaire, you’ll most likely use the same questions for all SaaS solutions. Your questionnaire should be crafted to ensure you’re asking about the most important elements of your Company-Wide Watermarks, such as validating evidence that frameworks are in place.
To save time creating a questionnaire, consider adopting a tool to help generate the questions. These tools keep you from recreating the wheel and tend to have much-needed management features to:
- Centrally store questionnaire answers
- Provide a grading system
- Enable note taking
- Set and know when the vendor is due for another evaluation
Step 3: Get Everyone Involved in the Vetting Process
Onboarding and maintaining the security of SaaS applications isn’t a single-department job. Finance, Legal, Procurement, IT, and sometimes more need to be engaged in the process. What’s more, any of these departments could find a reason to reject the purchase. That means a security review could be a waste of time in the first place.
If time is not a problem, however, it is safest to wait until all relevant stakeholders have reviewed the product. On the other hand, if you’re pressed for time to adopt a solution for an urgent need, move the security review to the top of the vetting process.
Step 4: Understand What Standardized Framework the Vendor Uses
If a SaaS vendor claims to use a standardized framework like NIST-CSF, they likely have a well-established security program and actively take security for customer data seriously. That’s a good sign on its own. Be sure to validate this claim by asking for the vendor’s security package. This should provide you with information on their relative data policies and support their security claims.
Think of it this way, consider data and information disposal. You can’t just run files through just any $80 Staples shredder. A framework will recommend a specific type of shredder to stay in compliance and require evidence that shredder is being used. Then, you know how information is being protected.
Step 5: Ensure Integrations are Secure
Integrations are a major aspect of cloud-based solutions. One tool works with another, and frankly, it’s incredibly convenient. However, integrations between tools and other systems can pose a certain risk as data passes between them. A security review is necessary to ensure integrations are safe.
Remember the fish tank incident? The same principle applies. Cybercriminals don’t need to attack you directly but simply find a side door like an unsecured integration.
That’s why you need to know that these connections are secure whether through data encryption, masking, or tokenization. You’ll also want to determine how integrations are authenticated to protect from unwanted access.
Additionally, your review should uncover what access is granted to your existing system. What exactly does the SaaS collect? Is it appropriate for the intended outcome or is it excessive?
Step 6: Conduct a Penetration Test
At this point in the review, you’re ready to validate your findings with a penetration test. Although this will depend on your use case, you’ll want to be sure you don’t see anything that didn’t come up in the vendor review.
Penetration testing involves an in-depth evaluation of all parts of a SaaS to identify vulnerabilities. Consider taking this step around the same time you develop your security review questionnaire.
Step 7: Finalize Your Security Review
At this point, you’re ready to put the findings in front of your internal stakeholders. The initial discussion should focus on all parties understanding the review results, determining the need for and obtaining any risk reviews, and summarizing any unresolved risks and/or questions for the vendor to address.
From there, the vendor must validate your claims and address the summarized findings of your security review to put any remaining concerns to rest. Any action taken by the vendor to remediate or mitigate a risk will likely need an additional one-off review from Security again to ensure the risk was addressed.
Oftentimes, a vendor commits to remediating a complex or complicated finding within a time period that your Security team, through the risk management program, can agree is acceptable. A security review is considered complete once all residual risks have been addressed through your risk management program resulting in a go/no-go decision.
Finally, you should compile your results into an auditable report for future review and should be stored for record keeping. If the vendor contract does not already have language to cover remediating any residual risks within committed timeframes, we recommend that such commitments be written into your contract to ensure legal liability for remediation.
Keep Your SaaS Secure with Zylo
Security reviews shouldn’t end after onboarding. They need to continue on a recurring basis as part of your Security team’s due diligence. All this ensures that your SaaS applications are as secure as when you onboarded them or identify risks missed in the past. This is true for every SaaS application in your environment – especially if they fall within your organization’s certification or regulatory compliance requirements.
The frequency of these reviews should be decided upon onboarding. Typically, this will fall around when a renewal is due, when a customer remediated a committed vulnerability fix, or annually. Plus, recurring reviews ensure SaaS applications remain within compliance between updates such as new features or coding.
Although security reviews can be a challenge to keep up with, Zylo can help you stay ahead.
Tracking and visibility are essential to SaaS security. Zylo’s Security Detail provides both. It allows you to know who owns an application while understanding the risk associated with your SaaS stack with an easy view of app compliance certifications.
What’s more, Zylo provides a comprehensive discovery of all the SaaS applications running in your environment. That includes high security risks like shadow IT that’s running under the radar of security and IT.
Better security starts with better visibility. Read here to learn more about how Zylo’s Discovery Engine helps you find all your SaaS.
How the Zylo Discovery Engine Powers the Most Comprehensive SaaS Management Platform
Learn More