The IT & SAM Leader’s Guide to Smarter Zoom License Management
Table of Contents ToggleShadow IT Risks You Cannot IgnoreHow to Find...
Back
Back
Search for Keywords...
Blog

Table of Contents
It may be easy to ignore shadow IT risks from hidden employee-acquired applications and subscriptions lurking in your company’s tech stack. But the longer it goes unaddressed, the bigger the risk grows.
Shadow IT is defined as business applications used by departments, teams, or employees without the direct knowledge or awareness of the IT team. Because these tools frequently do not undergo the same risk assessment and vetting process IT uses for tools, shadow IT can represent a significant risk to the organization’s security.
But as more companies embrace SaaS for business software, the growth of shadow IT – and its inherent security risks – is often a direct result. As CIODive’s Roberto Torres notes, “With a sharper focus on cloud-based apps, alongside the pivot to distributed work, comes greater security exposure.”
The wide adoption of SaaS — from small business to enterprise organizations — has made shadow IT more prevalent.
Gartner projects that SaaS spend will grow to more than $299B in 2025 – an 19.3% increase from 2022. This tracks closely with the cloud growth Bessemer Venture Partners has measured over the last several years.
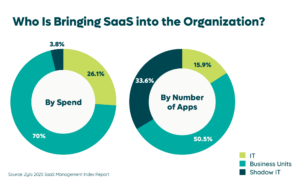
With one in fifteen employees expensing SaaS and employee purchases comprising more than one-third of SaaS applications, it’s clear that shadow IT risks are a growing concern.
We’ve identified five primary risks that organizations should be aware of. This isn’t an exhaustive list, but instead reflects what we see as the biggest challenges for SaaS-sourced shadow IT for the IT organization.
When business units and employees procure and use SaaS applications without the knowledge or permission of the IT team, IT leaders can no longer assume they retain absolute control over their environment. When applications don’t receive vetting or security review, potential risks multiply. One of the most significant shadow IT dangers: Increased risk for a data breach. The average data breach costs more than $4.88M according to an IBM study.
How does undiscovered shadow IT and specifically SaaS contribute to this increased risk? When teams or employees acquire software unbeknownst to IT (or the primary tech managing team), it’s not reviewed or vetted. However, since shadow IT is being used in the context of business objectives within the organization, it’s highly likely that the application contains some form of business-related data.
Whether it be personally identifiable information (PII) of customers, intellectual property, or simply the users’ business email address used at log-in, each of these forms of data can be potential vulnerabilities that should be addressed to mitigate risk.
The fact that these applications exist outside of IT’s awareness or control demonstrates how unlikely they are to be integrated into user-based security processes such as single sign-on platforms.
And a data breach doesn’t necessarily have to originate from malice. According to the IBM-study, nearly half of all breaches come from inadvertent errors such as human mistakes or system glitches.
For industries regulated by laws pertaining to privacy, data handling, or other rules such as health information, the growth of shadow IT in SaaS applications represents potential violations and danger for your organization. In these environments, teams and employees using SaaS without having the applications vetted for regulatory compliance could lead to fines in the tens of millions of dollars.
For example, the European Union’s General Data Protection Regulation (GDPR) regulates what businesses can and cannot do with privacy data related to the more than 500 million people living within the EU’s jurisdiction. But, GDPR carries global implications – including businesses operating in the United States. Any entity doing business with an EU citizen must abide by the EU’s rules, regardless of the company’s location. Unmanaged SaaS acquisition (shadow IT) compounds the risk of non-compliance with GDPR.
Other regulations such as the Health Insurance Portability and Accountability Act (HIPAA), Sarbanes-Oxley, and the California Consumer Privacy Act all have wide-ranging implications for the use of consumer data and privacy – and specifically any application potentially storing or transferring this information.
As a segment of business spending, SaaS revenue has grown by double digits for several consecutive years. Gartner projections show that in 2021, SaaS applications accounted for more than $145B in spending. By the end of 2025, Gartner predicts SaaS will capture more than $299B in spending. Few software categories have grown or continue to grow more quickly than SaaS.

A primary reason for this explosive growth is the fact that the majority of SaaS application purchases no longer originate in IT budgets but in lines of business (LOB) budgets. In fact, IDC projects that 70% of all application purchases are now sourced from business budgets. If and when these purchases occur without IT’s involvement, there’s a high likelihood that they become shadow IT.
And it’s not just LOBs that are becoming primary SaaS consumers, now more than ever employees are likely to purchase SaaS applications for business use via credit cards and expense reimbursement.
Zylo data shows that about one-fifth of all employees have purchased SaaS applications via credit cards and expense reimbursement at an average cost of about $600 each. Unchecked, unmonitored, and unmanaged, these employee-created costs can quickly spiral out of control.
However, despite some danger, it’s important to note that not all shadow IT is necessarily bad. Employees and departments frequently have legitimate reasons to acquire software independent of IT including speed of acquisition and deployment, low cost, and ease of use.
Another risk to SaaS cost management is the number of ways shadow IT creates detrimental impacts to spending. When unchecked, SaaS-based shadow IT creates multiple avenues for inefficient or ineffective spending to grow.
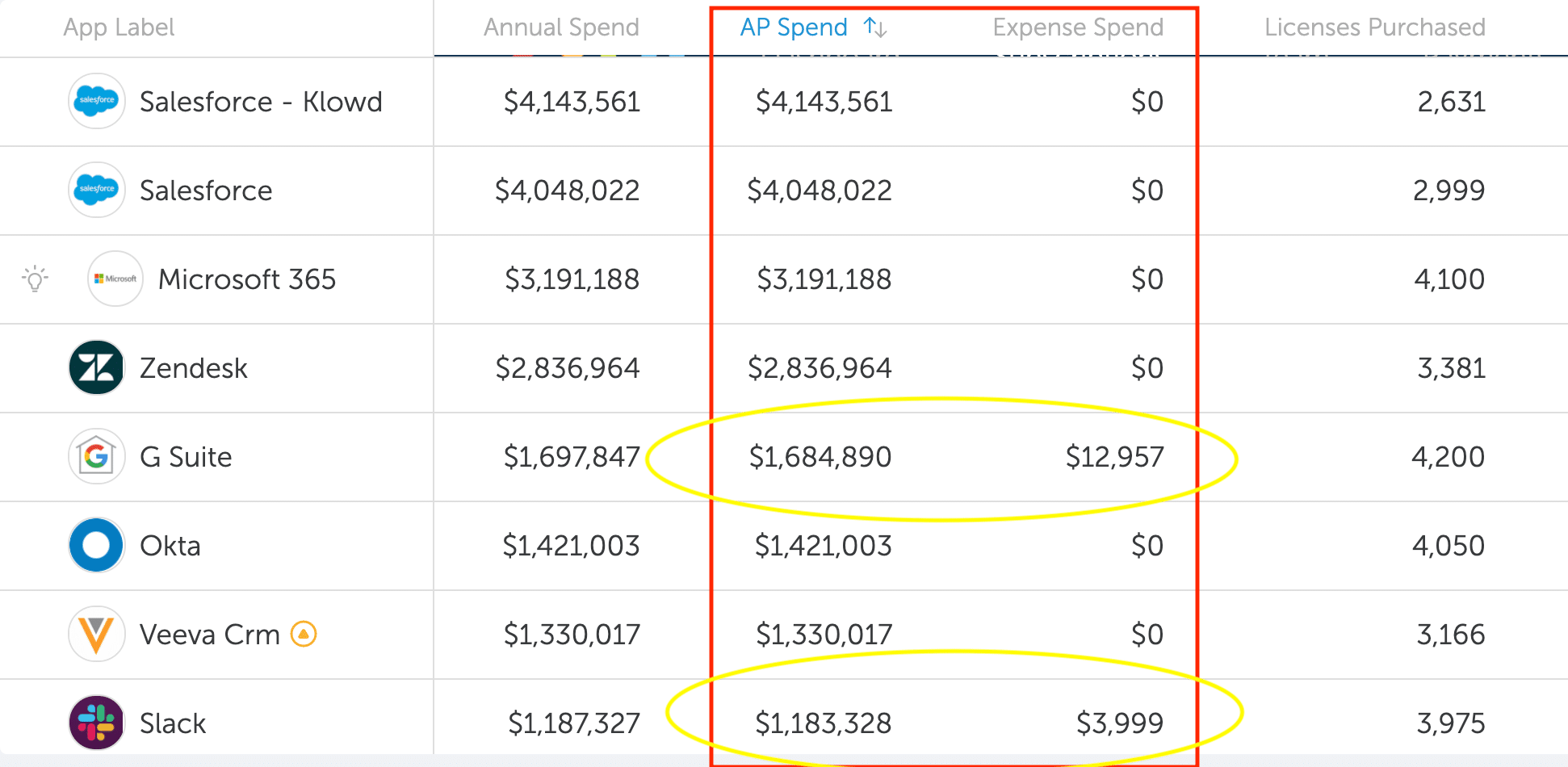
Multi-sourced spending, where SaaS applications are purchased by both the business in direct vendor transactions via Accounts Payable and by employees in expense reimbursement, is a frequent problem with SaaS applications in large organizations.
This leads to multi-sourced spend where the business actually maintains two separate instances of the same tool, one as a centrally managed and directly purchased application and the other as an unknown and unneeded instance.
Application duplication is another factor in increased costs due to inefficient spending. This occurs mainly when two separate teams or employees purchase the same product without knowledge of the other. When these purchases occur as shadow IT, the organization is robbed of the consolidated buying power and value that could be leveraged by accounting for all needed users.
Lastly, functional overlap occurs when multiple teams or employees acquire SaaS applications that perform the same function. Take video conferencing as an example. If two business units within the same organization purchase different video conferencing tools – and the tools remain hidden as shadow IT – buying power again is reduced, and intra-organizational friction may result if the teams ever need to confer with each other.
A common feature of SaaS applications is the existence of auto-renewal clauses in the purchase agreement or contract.
While intended to ensure continuity of service, when SaaS applications with auto-renewal clauses accumulate as shadow IT, the result is frequently little to no central planning of renewals, and therefore increased costs. Zylo data shows that the average large enterprise undergoes 476 SaaS renewals annually, or two per business day.
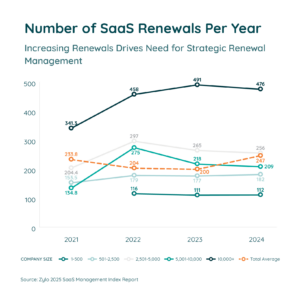
Without a way to discover these applications and manage renewal dates and notification periods proactively, businesses are often at the mercy of reacting to automatic renewals rather than planning them. Frequently the outcome is the business purchases the SaaS application or subscription for another term unintentionally, leading to unexpected and increased costs.
The first step toward reducing shadow IT risks is a robust SaaS discovery process, like Zylo’s Discovery Engine. This process should accurately illuminate the entire scope of an organization’s SaaS application inventory, including otherwise hidden applications.
This can be accomplished in a number of ways:
IT or the technology managing team surveys employees and users about which SaaS applications they maintain. They capture important information such as spending amounts, renewal dates, notification periods, subscriptions, features, and license information. While spreadsheets are low-cost, the drawback of this approach is that the information is outdated quickly and each update requires manual effort.
A CASB provides insights into application use by sitting between cloud service users and cloud applications, and monitors all activity and enforces security policies. This solution ensures security and monitoring between users and the connected cloud applications. However, it’s limited in its ability to discover non-connected applications.
Similar to a CASB, SSO systems act as a bridge between the user and connected applications. However, like a CASB, it cannot detect unconnected applications, which are highly likely in today’s landscape of increasingly distributed teams and remote work.
One of the most thorough discovery methods is financial discovery for shadow IT. This process depends on the ability to access and process large volumes of purchase data (typically found in expense management systems). The analysis can be augmented by machine learning, as well as other forms of discovery to root out freeware shadow IT.
A drawback to this discovery method may be the reluctance to share financial information, however, accreditations such as SOC II Type 2, which verifies robust security and data handling procedures, can help alleviate this concern.
Zylo’s Discovery Engine is a comprehensive discovery tool that finds 100% of an organization’s SaaS. Combine with our SOC II Type 2 certification, it’s a way to get a complete picture and sniff out shadow IT – and the risks that come with it.
Along with initial discovery and mitigation, stymying new growth of shadow IT is a continual process. Gartner has estimated that as much as 30% to 40% of IT spending in large enterprises is shadow IT, which can make it difficult to address current challenges while preventing future ones.
One of the most effective ways to address SaaS-based shadow IT is implementing a holistic SaaS management program that addresses the range of challenges raised by SaaS.
At Zylo, we recommend deploying a SaaS Management Lifecycle that addresses the entire lifecycle of managing SaaS in four distinct phases:
Discover – Creating the processes necessary to discover SaaS-based shadow IT and continually monitor the tech environment for new instances.
Optimize – Eliminating inefficient purchasing processes and leveraging utilization data to optimize spending and the SaaS inventory as a whole.
Plan – Designing a proactive and collaborative SaaS renewal process, as well as controlling SaaS inventory growth using insights gleaned from data.
Govern – Establishing internal processes such as software review boards or distribution of business application management (rather than IT alone) to teams to ensure policies prevent shadow IT.
As a software category, SaaS is here to stay. Businesses must find new ways to transform the challenges of shadow IT into new opportunities to innovate.
See how the world’s most innovative companies have deployed SaaS management to control costs and risks from shadow IT. Schedule a demo of the Zylo SaaS Management platform.

Table of Contents ToggleShadow IT Risks You Cannot IgnoreHow to Find...

Table of Contents ToggleHow FinOps Teams Commonly Understand SaaS—and What’s MissingSaaS...

Table of Contents ToggleWhat Is an E-Commerce Tech Stack?Why Your E-commerce...
Table of Contents ToggleShadow IT Risks You Cannot IgnoreHow to Find...
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |
