Table of Contents
SaaS has changed the way we work. There is no doubt. Every year, on-premise software continues to lose out to SaaS to cover enterprise software needs. However, despite the myriad of benefits, SaaS still comes with risks to your business.
Shadow applications pose potentially costly and embarrassing risks. The average cost of a data breach in the U.S., according to IBM, has grown to a considerable $4.88M.
And this isn’t counting the damage a breach can cause to a company’s reputation.
“It’s very embarrassing,” David Stoicescu, Chief Information Security Officer at Deepwatch, shared with us on SaaSMe Unfiltered. “When I look at it from my perspective, it’s easy to say, ‘Well, I didn’t know.’ But when somebody reads about it in an article, it comes across like, ‘You don’t run a competent program. Clearly, you don’t know what you’re doing.’ Perception makes and breaks people and companies and reputation.”
As such, due to the risks to a company’s data, selecting a SaaS solution can vary widely depending on the information you intend to share with a provider paired with your company’s compliance policies, customer contracts, and industry compliance requirements. It’s important to ask yourself, “What security measures should I look for in SaaS?”
That’s why today we’re going to look at common security risks you should watch for with your vendors and how your organization can maintain compliance.
What Security Measures Should I Look for in SaaS?
Access Management
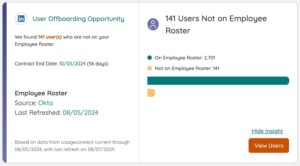
A simple, but nonetheless serious, security risk is a matter of access. You need complete knowledge of who is using the application as well as if it’s compatible with your company’s SSO/SAML provider. Otherwise, you risk losing track of who is able to access certain, and potentially sensitive, company information. A serious data breach could be one compromised password away.
It’s important to centralize access requirements and ensure that your portfolio doesn’t include one-off applications with limited access. Otherwise, you may find yourself with an application that no one in your organization has access to, especially if it was not managed under SSO and SAML. What’s more, an employee that leaves the company may retain access and the relevant log-in information to do so. Needless to say, that would put your organization at serious risk of data loss.
That’s why SaaS-mindful offboarding isn’t a convenience, it’s a necessity.
Information Sharing
When vetting new SaaS applications, it’s important to note any information-sharing capabilities. If the application does share information, does it do so using secure methods? Does it line up with the compliance standards of your industry? It’s better to know the answers to these questions now rather than suffer a data breach later.
On the subject of information sharing, it’s equally important to know if the application in question does anything else with your data. That’s to say, is the vendor utilizing your data in other ways? Many SaaS solutions make revenue in ways other than your direct payments. In fact, many SaaS vendors profit by selling, sharing, or utilizing the data that flows through their platform.
Depending on your industry, this can pose a compliance risk. Ensure you understand what you’re agreeing to when you create an account with any vendor.
Data Transmission and Retention
Now that we’ve covered who has access to your data and how it’s being used, what about where your data is being stored? Ever since the world shifted to storing data in “the cloud,” data storage has become an easy thing to overlook.
However, there is no real cloud. Your data is in a physical data bank somewhere in the world.
Never assume that the application you’re using is transmitting and storing your data in a compliant and secure way. Ensure that it is. Take the time to understand how and where your data is transmitted and stored with your SaaS provider. For example, while many providers base their product operations within a single country, they may utilize sub-processors in multiple countries which may fall outside of compliance for your company.
Once you understand how and where your data is being stored, there’s the matter of how long your data is being stored.
Naturally, you’ll want data to be stored with an application for as long as you’re using it, but what about after you terminate a license with a vendor or stop using their product? If you’re like most companies, you’ll want that data cleared once you’re finished with a service. As such, you’ll want to ensure that every application removed from your portfolio is properly offboarded as part of your regular SaaS management policies. This includes deleting, or requesting deletion, of the information relevant to your account with a vendor.
Additionally, this is more than just your data that is flowing through the application. Rather, it includes your employees’ information utilized within the solution. Even though this information may seem inconsequential now, it could pose a risk later down the line.
Disaster Recovery and Availability
It’s easy to take something for granted until it stops working. As such, a core tenet of security is understanding availability.
Consider the potential impact if a given SaaS application was suddenly unavailable or malfunctioning. Will this impact your customers? How will it affect your business? Understanding these risks now allows you to build contingencies today for a potential disaster tomorrow. It is always better to be prepared.
Furthermore, in the event of a gap in service, how and when will the provider inform you there is a service issue with their product? Is this a matter of contract or purely a courtesy? Ideally, look for services that not only provide a site to check service availability but are also contractually committed to providing regular updates during outages. Consider the provider’s service level agreements (SLAs) and establish a complete understanding of their contractual obligations and what you will receive if these obligations are not met.
So, we’ve considered gaps in availability, but what if a vendor experiences a complete disaster? A disaster for a SaaS solution critical to your company has the potential to have a snowballing impact on your company – damaging public relations and the overall service you provide.
When selecting an application and negotiating a contract, consider inquiring about the vendor’s contingency plans for such an event. Always know and understand how your SaaS provider will come back from disasters and what data they’ll be able to retrieve.
The metrics used to track recovery SLAs are referred to as:
- RTO – Recovery Time Objective refers to how long it would take to recover from a worst-case disaster.
- RPO – Recovery Point Objective is what state the system and your data will be in when recovery is complete.
Regardless, know if your company policies and obligations are still met during a disaster – this information will typically be described in your MSA and/or DPA with your SaaS provider.
Auditability and Logging
Do you know who accessed your instance of a SaaS solution, what they did, and when? This level of visibility is where many SaaS applications fall short as this type of information tends to require significant investment in storage capacity. However, this information is still essential for security investigations within your company rather than relying on the SaaS provider’s promise of due diligence.
Additionally, consider if logging information can be exported to your own company’s security system such as SIEM or centralized logging. This saves organizations from relying on logs within a given SaaS solution which run the risk of tampering via a bad actor. Transmitting these logs into your environment allows you to account for any deviations during an investigation.
Although this logging and audibility are uncommon, it is still worth vetting with your provider before committing to a contract.
Evolving Your SaaS Governance Framework for the Digital Workplace
Learn MoreHow to Ensure All Applications are in Compliance
Now that we’ve looked at some of the significant security risks you should vet with your SaaS vendor, let’s consider what you can do to ensure compliance in all of your applications.
This will require you to establish compliance policies based on the regulations and compliance requirements of your industry. These policies should cover how users engage with SaaS applications and address third-party risks such as API connections and sub-processors.
Conducting a security review or risk assessment with a vendor will allow you to identify, and address, any potential risks before purchasing or sharing sensitive information with that application. This entails investigating a service for all of the security risks we discussed above as part of your standard security checklist. It’s also worth mentioning that it is best practice to do this in advance of signing a contract with the vendor.
Additionally, establishing compliance policies using common industry frameworks, such as NIST CSF or ISO27001, allow for alignment and awareness across your organization and customer base.
Overall, this involves creating policies and/or processes to handle:
- Communication – Communicating with stakeholders is vital to any system of SaaS management, and potentially one of the most challenging policies to effectively build. Without communication, employees won’t know what they need to do to work within your compliance policies.
- Shadow IT – And when employees don’t know what they need to do or what to watch for in terms of security measures, we get shadow IT – applications running under the radar of your company and creating meaningful security risks to your organization. Rooting out this shadow IT is necessary to avoid data breaches, maintain your company’s compliance, and much more.
- Application Visibility – Even after communication and shadow IT are handled, you will still need to ensure your employees understand every relevant piece of SaaS that your organization uses.
To achieve all of this, you will need a SaaS management tool that performs comprehensive and ongoing discovery within your SaaS portfolio. That means rooting out shadow IT, tracking applications’ compliance with certifications such as SOC2 and GDPR, and much more to help you keep security at the forefront of SaaS management.
Prioritize Security When Purchasing SaaS
If you take anything away from this, know that there are many security risks to account for. No longer will you have to ask yourself, “What security measures should I look for in SaaS,” next time you’re vetting a new vendor. You’ll have this checklist to go by!
It does go without saying that a comprehensive approach to SaaS management is required to protect your business. Thankfully, you don’t have to take on this daunting task alone.
Zylo allows companies to easily achieve complete visibility of their entire SaaS portfolio to discover shadow IT wherever it hides and fend off security risks wherever they lurk.