
SaaS Predictions for 2026 Signal a Shift in Spend and Governance
Table of Contents ToggleWhat Is Shadow IT and Where Does It...
Back
Back
Search for Keywords...
Blog

Table of Contents
SaaS is easy to buy—almost frighteningly so. Go to any website, click a button, and punch in your credit card number. Voila! You’re in.
We all have a co-worker (or two) who has done this, which may seem innocuous. But the reality is that one in fifteen (6.6%) employees in your organization is expensing software. This leads to what we call shadow IT, and at a time with swift AI adoption in the workplace, shadow AI.
What is shadow IT? In this blog, we’ll define what it is, where it comes from, the pros and cons, and how to eliminate it.
Shadow IT, also known as shadow applications, is software purchased by individuals or lines of business without IT’s knowledge. We find that shadow IT accounts for just 3.8% of an organization’s SaaS spend. However, it amounts to a significant 33.6% of your SaaS portfolio. Something’s out of line, right?
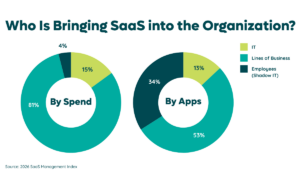
Before we look at combating shadow IT, let’s look at all the effects it can have on your SaaS stack and SaaS spending—for good and for ill. Shadow IT has a pretty scary name, sure, but it doesn’t always have to be a Nazgûl stalking your IT department. It can have specific benefits that justify its existence, but it does have plenty of risks associated with it that justify its regulation, as well.
We’ve spent most of this article discussing how scary shadow IT is, so you’re probably doubtful of our claim that it can benefit your company. Let’s prove our point. Shadow IT has three main benefits:
Alongside those benefits, shadow IT has its fair share of risks — trust us. Between unvetted apps, untracked purchases, and unprocessed security policies, shadow IT can pose huge threats to your company’s security and spend. Shadow IT has three main risks you need to keep in mind.
We could talk all day about the increased cost of shadow IT, but we’ll try and boil it down to a few key points:
Shadow IT means applications aren’t being vetted by your IT department. Yet, SaaS applications almost always deal with your business’s data. In fact, our data shows that expensed software (a.k.a. shadow IT) are riskier. Nearly 61% have “Poor” or “Low” Cloud Confidence Score, or risk score.
On the surface, employee purchases may seem innocuous and harmless. But that truth is that they pose more risk thank you think.
Shadow IT can be seriously damaging to your company, because it opens you up to potentially devastating data breaches. That’s not even mentioning the ones that happen just because of human error! IT vetting applications can save your company a whole lot of money and trouble.
Alongside risks of data breaches, unvetted applications can lead to your company unwittingly breaching regulations, most notably the Health Insurance Portability and Accountability Act (HIPAA) and the General Data Protection Regulation (GDPR). This can cost you a ton in fines and legal issues.
To eliminate shadow IT, you must first identify it. With the process of SaaS inventory management, you can discover and tracj shadow applications. Then, limit shadow IT by actively monitoring it.
While you could look at your expense reports to find unsanctioned software purchases, you won’t find everything. That’s because 51% of expenses are miscategorized as something other than software.

By following the money, regardless of the procurement process, organizations can identify a comprehensive view of their shadow IT spending. No matter what tool you use, visibility is key. So the more effective the tool, the better.
Many businesses now utilize SaaS management tools like Zylo, which provides a near 100% accuracy for SaaS detection and categorization.
Once you’ve uncovered your SaaS stack, you can build relationships with SaaS buyers in your company and get them in line with an overall strategy. Start by identifying the SaaS stakeholders and establish connections with them. Building these relationships helps you establish trust and communication. It results in unifying stakeholders on your strategies and tactics, and supports an open door policy where they they can reach out to you with questions and concerns related to SaaS.
With visibility achieved and stakeholders unified, you have all the information and perspectives you need to build a governance strategy.
While SaaS purchasing is decentralized, we’re seeing more and more IT organizations centralize SaaS governance. Having policies that regulate software purchasing keeps IT in the loop and reduces shadow IT and its associated costs.
“Freedom within a Framework” is an effective approach where parameters are established to avoid opening the organization up to unnecessary risk or spend. At the same time, it also enables employees to have the freedom to choose their tools.
Evolving Your SaaS Governance Framework for the Digital Workplace
Learn MoreNo longer do you have to ask: what is shadow IT? It’s a natural occurrence in any organization.
Sure, it has its risks. But for some companies, the benefits outweigh the risks if they have visibility into their entire SaaS estate.
When you have complete visibility and establish and communicate governance policies, you can reduce compliance, security, and financial risks while still empowering employees to unlock productivity, creativity, and collaboration.
Shadow IT can be your friend, you just need to set boundaries with it.
If you want to maximize visibility and take the next steps with your company’s shadow IT, you need the right tools. Learn how Zylo’s AI-powered Discovery Engine can detect shadow IT in your organization.

Table of Contents ToggleWhat Is Shadow IT and Where Does It...

Table of Contents ToggleWhat Is Shadow IT and Where Does It...

Table of Contents ToggleWhat Is Shadow IT and Where Does It...

Table of Contents ToggleWhat Is a SaaS Savings Pipeline?Why Managing SaaS...
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |